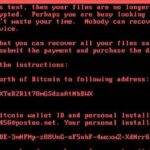
The latest splash has been made by the Petya or NotPetya Ransomware that exploded in Ukraine and is infecting companies all over the World. It’s getting some people in deep trouble as there’s no way to recover the files once encrypted. The malware seems to be trying to hide its intent as it doesn’t really […]
Malware
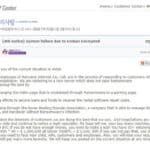
South Korean Webhost Nayana Pays USD1 Million Ransom
So far this Nayana payout is the biggest ransomware payment I’ve seen reported, there’s probably some bigger ones been paid but kept undercover. Certainly a good deal for the bad actors in this play, and well using an outdated Kernel along with PHP and Apache versions from 2006 you can’t feel too sorry for Nayana. […]
maltrail – Malicious Traffic Detection System
Maltrail is a malicious traffic detection system, utilizing publicly available (black)lists containing malicious and/or generally suspicious trails, along with static trails compiled from various AV reports and custom user-defined lists, where trail can be anything from domain name (e.g. zvpprsensinaix.com for Banjori malware), URL (e.g. http://109.162.38.120/harsh02.exe for known malicious executable), IP address (e.g. 185.130.5.231 for […]
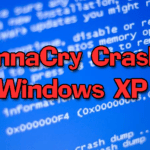
Windows XP Too Unstable To Spread WannaCry
Not a super serious article this one, but I found it very entertaining – apparently, Windows XP has a BSOD (Blue Screen of Death) when faced with a WannaCry infection. There’s a very extension analysis of WannaCry here where this information comes from WannaCry: Two Weeks and 16 Million Averted Ransoms Later. Yes, WannaCrypt can […]
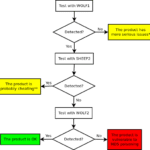
sheep-wolf – Exploit MD5 Collisions For Malware Detection
sheep-wolf is a tool to help you Exploit MD5 Collisions in software, specially malware samples which are commonly detected using MD5 hash signatures. and then a malicious one (Wolf) that have the same MD5 hash. Please use this code to test if the security products in your reach use MD5 internally to fingerprint binaries and […]