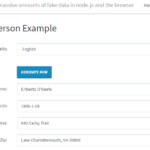
faker.js is a tool to generate fake data in Node.js and in the browser, it has a lot of different data types to enable you to generate very customised and complete sets of fake or mock data for testing purposes. It also supports multiple languages and locales and can generate a lot of data types […]
Secure Coding
Secure coding is very important in software development to ensure code security is high using techniques such as static analysis, code auditing and dynamic analysis to ensure safe coding practices are followed.

What Tools can be used for Secure Coding?
There are a variety of tools to ensure code safety, mostly based on source code auditing and static analysis.
The options available really depend on the language being used with some tools focusing on many languages such as Yasca – Multi-Language Static Analysis Toolset or specialist tools focusing on a single language like Brakeman – Static Analysis Rails Security Scanner.
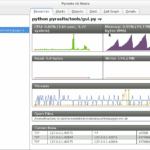
pyrasite – Inject Code Into Running Python Processes
pyrasite is a Python-based toolkit to inject code into running Python processes. pyrasite works with Python 2.4 and newer. Injection works between versions as well, so you can run Pyrasite under Python 3 and inject into 2, and vice versa. Usage
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 |
usage: pyrasite [-h] [--gdb-prefix GDB_PREFIX] [--verbose] [--output OUTPUT_TYPE] pid [filepath|payloadname] pyrasite --list-payloads pyrasite - inject code into a running python process positional arguments: pid The ID of the process to inject code into filepath|payloadname The second argument must be a path to a file that will be sent as a payload to the target process or it must be the name of an existing payload (see --list-payloads). optional arguments: -h, --help show this help message and exit --gdb-prefix GDB_PREFIX GDB prefix (if specified during installation) --verbose Verbose mode --output OUTPUT_TYPE This option controls where the output from the executed payload will be printed. If the value is 'procstreams' (the default) then the output is sent to the stdout/stderr of the process. If the value is 'localterm' then the output is piped back and printed on the local terminal where pyrasite is being run. --list-payloads List payloads that are delivered by pyrasite For updates, visit https://github.com/lmacken/pyrasite |
You can download pyrasite here: pyrasite-2.0.zip Or read more here.
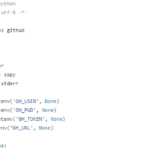
Github Dorks – Github Security Scanning Tool
Github search is quite a powerful and useful feature and can be used to search for sensitive data in repositories, this Github security scanning tool comes with a collection of Github dorks that can reveal sensitive personal and/or other proprietary organisational information such as private keys, credentials, authentication tokens and so on. github-dork.py is a […]
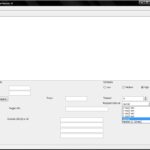
Powerfuzzer – Automated Customizable Web Fuzzer
Powerfuzzer is a highly automated and fully customizable web fuzzer (HTTP protocol based application fuzzer) based on many other Open Source fuzzers available and information gathered from numerous security resources and websites. It was designed to be user-friendly, modern, effective and to work consistently. It is also designed and coded to be modular and extendable, […]
Wycheproof – Test Crypto Libraries Against Known Attacks
Project Wycheproof is a tool to test crypto libraries against known attacks. It is developed and maintained by members of Google Security Team, but it is not an official Google product. At Google, they rely on many third party cryptographic software libraries. Unfortunately, in cryptography, subtle mistakes can have catastrophic consequences, and they found that […]