Malcom is a Malware Communication Analyzer designed to analyze a system’s network communication using graphical representations of network traffic, and cross-reference them with known malware sources. This comes handy when analyzing how certain malware species try to communicate with the outside world. Malcom Malware Communication Analyzer Features Malcom can help you: Detect central command and […]
Python
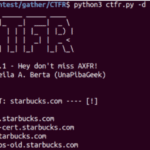
CTFR – Abuse Certificate Transparency Logs For HTTPS Subdomains
CTFR is a Python-based tool to Abuse Certificate Transparency Logs to get subdomains from a HTTPS website in a few seconds. You missed AXFR technique didn’t you? (Open DNS zone transfers), so how does it work? CTFR does not use dictionary attack or brute-force attacks, it just helps you to abuse Certificate Transparency Logs. What […]
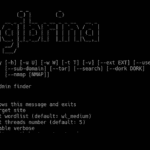
Cangibrina – Admin Dashboard Finder Tool
Cangibrina is a Python-based multi platform admin dashboard finder tool which aims to obtain the location of website dashboards by using brute-force, wordlists, Google, Nmap and robots.txt. It is multi-threaded, supports modifying your user agent, using a TOR proxy, custom dorks, Nmap integration and can use both DuckDuckGo and Google. Cangibrina Admin Dashboard Finder Requirements […]
Metta – Information Security Adversarial Simulation Tool
Metta is an information security preparedness tool in Python to help with adversarial simulation, this can help you check various detection and control capabilities within your organisation. This project uses Redis/Celery, python, and vagrant with virtualbox to do adversarial simulation. This allows you to test (mostly) your host based instrumentation but may also allow you […]
Powershell-RAT – Gmail Exfiltration RAT
Powershell-RAT is a Python-based Gmail exfiltration RAT that can be used a Windows backdoor to send screenshots or other data as an e-mail attachment. This RAT will help you during red team engagements to backdoor any Windows machines. It tracks the user activity using screen capture and sends the information to an attacker as an […]