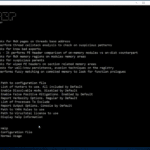
Memhunter is an Automated Memory Resident Malware Detection tool for the hunting of memory resident malware at scale, improving the threat hunter analysis process and remediation times. It’s a self contained binary that can be deployed and managed at scale, does not use memory dumps and relies purely on memory inspection to do its work. […]
Forensics
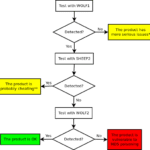
sheep-wolf – Exploit MD5 Collisions For Malware Detection
sheep-wolf is a tool to help you Exploit MD5 Collisions in software, specially malware samples which are commonly detected using MD5 hash signatures. and then a malicious one (Wolf) that have the same MD5 hash. Please use this code to test if the security products in your reach use MD5 internally to fingerprint binaries and […]
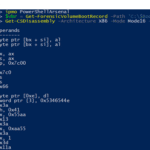
PowerShellArsenal – PowerShell For Reverse Engineering
PowerShellArsenal is basically PowerShell for reverse engineering in a module format. The module can be used to disassemble managed and unmanaged code, perform .NET malware analysis, analyse/scrape memory, parse file formats and memory structures, obtain internal system information, etc. PowerShellArsenal is comprised of the following tools: Disassembly – Disassemble native and managed code. MalwareAnalysis – […]
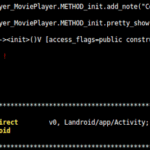
Androguard – Reverse Engineering & Malware Analysis For Android
Androguard is a toolkit built in Python which provides reverse engineering and malware analysis for Android. It’s buyilt to examine * Dex/Odex (Dalvik virtual machine) (.dex) (disassemble, decompilation), * APK (Android application) (.apk), * Android’s binary xml (.xml) and * Android Resources (.arsc). Androguard is available for Linux/OSX/Windows (Python powered). Features Map and manipulate DEX/ODEX/APK/AXML/ARSC […]
Volatility Framework – Advanced Memory Forensics Framework
The Volatility Framework is an an advanced, completely open collection of tools for memory forensics, implemented in Python under the GNU General Public License, for the extraction of digital artifacts from volatile memory (RAM) samples. The extraction techniques are performed completely independent of the system being investigated but offer visibility into the runtime state of […]