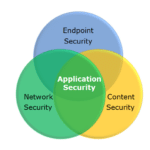
In the world of web application security systems, there exists a myriad of systems to protect public-facing services in any number of ways. They come packed with all the elements necessary to play an action-packed round of buzzword bingo, but they often overlap in some ways that may make them sometimes seem similar. After the second […]
web-application-security
Web Application Log Forensics After a Hack
Sites get hacked, it’s not pleasant but it happens. A critical part of it, especially in my experience, has been the web application log forensics applied directly after an attack. You can usually piece together what happened, especially if the attacker doesn’t rotate IP addresses during the attack. With a little poking around and after […]
Defence In Depth For Web Applications
Defence in depth for web applications is something that not many companies apply even though the model itself is nothing new. Defence in depth refers to applying security controls across multiple layers, typically Data, Application, Host, Internal Network, Perimeter, Physical + Policies/Procedures/Awareness. Defence in depth is a principle of adding security in layers in order […]
ModSecurity – Open Source Web Application Firewall
ModSecurity is an open source web application firewall (WAF) module that is cross platform capable. Known as the “Swiss Army Knife” of WAFs, it enables web application defenders to gain visibility into HTTP(S) traffic and provides a power rules language and API to implement advanced protections. ModSecurity is a toolkit for real-time web application monitoring, […]
WATOBO – The Web Application Security Auditing Toolbox
WATOBO – The Web Application Security Auditing Toolbox – is intended to enable security professionals to perform highly efficient (semi-automated ) web application security audits. It is capable of passive as well as active scanning and this latest is its real value added. It enables to automatize the discovery of common vulnerabilities (XSS, LFI, SQL […]