exe2powershell is used to convert EXE to BAT files, the previously well known tool for this was exe2bat, this is a version for modern Windows. This will convert any binary file (*.exe) to a BAT file, the resulting BAT file contains only echo commands followed by a PowerShell command to re-create the original binary file. […]
Windows Hacking
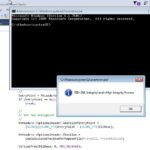
UACMe – Defeat Windows User Account Control (UAC)
UACme is a compiled, C-based tool which contains a number of methods to defeat Windows User Account Control commonly known as UAC. It abuses the built-in Windows AutoElevate backdoor and contains 41 methods. The tool requires an Admin account with the Windows UAC set to default settings. Usage Run executable from command line: akagi32 [Key] […]
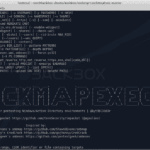
CrackMapExec – Active Directory Post-Exploitation Tool
CrackMapExec (a.k.a CME) is a post-exploitation tool that helps automate assessing the security of large Active Directory networks. Built with stealth in mind, CME follows the concept of “Living off the Land”: abusing built-in Active Directory features/protocols to achieve its functionality and allowing it to evade most endpoint protection/IDS/IPS solutions. CME makes heavy use of […]
Windows XP Too Unstable To Spread WannaCry
Not a super serious article this one, but I found it very entertaining – apparently, Windows XP has a BSOD (Blue Screen of Death) when faced with a WannaCry infection. There’s a very extension analysis of WannaCry here where this information comes from WannaCry: Two Weeks and 16 Million Averted Ransoms Later. Yes, WannaCrypt can […]
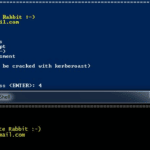
PowerMemory – Exploit Windows Credentials In Memory
PowerMemory is a PowerShell based tool to exploit Windows credentials present in files and memory, it levers Microsoft signed binaries to hack Windows. The method is totally new. It proves that it can be extremely easy to get credentials or any other information from Windows memory without needing to code in C-type languages. In addition, […]