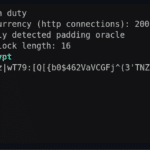
padre is an advanced exploiter and Padding Oracle attack tool that can be deployed against CBC mode encryption.
Hacking Tools
Hacking Tools are pieces of software or programs created to help you with hacking or that users can utilise for hacking purposes.
Examples include Wep0ff – Wifi Cracking Tool, Brutus Password Cracker, wwwhack Web Hacking, THC-Hydra Network Login Hacking and pwdump/fgdump Windows Password Dumping Tools.

You can find the latest and best hacking tools below and more on Wikipedia.
Script Kiddie Hacking Tools
There are various tools that are classified as too easy to use, or too automated and these fall into the category of Script Kiddie Tools. These are people who just follow instructions from a manual or tutorial without really understanding the technology or process happening.
Examples of these tools would mainly be password cracking tools like Cain and Abel Password Cracker, Brutus Password Cracker and John the Ripper for Password Cracking.
DataSurgeon – Extract Sensitive Information (PII) From Logs
DataSurgeon (ds) is a versatile tool designed to Extract Sensitive Information (PII) From Logs, it’s intended to be used for incident response, penetration testing, and CTF challenges.
Pwnagotchi – Maximize Crackable WPA Key Material For Bettercap
Pwnagotchi is an A2C-based “AI” leveraging bettercap that learns from its surrounding WiFi environment to maximize crackable WPA key material it captures
Socialscan – Command-Line Tool To Check For Email And Social Media Username Usage
socialscan is an accurate command-line tool to check For email and social media username usage on online platforms, given an email address or username, socialscan returns whether it is available, taken or invalid on online platforms. Other similar tools check username availability by requesting the profile page of the username in question and based on […]
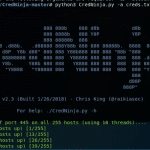
CredNinja – Test Credential Validity of Dumped Credentials or Hashes
CredNinja is a tool to quickly test credential validity of dumped credentials (or hashes) across an entire network or domain very efficiently. At the core of it, you provide it with a list of credentials you have dumped (or hashes, it can pass-the-hash) and a list of systems on the domain (the author suggests scanning […]