Wep0ff is new WEP Key Cracker that can function without access to AP, it works by mounting a fake access point attack against WEP-based wireless clients.
It uses a combination of fragmentation and evil twin attacks to generate traffic which can be used for KoreK-style WEP-key recovery.
This tool can be used to mount fake access point attack against WEP-based wireless clients.
This code tested patched madwifi-old drivers with athraw support but also works with madwifi-ng. With madwifi-ng you need to create two virtual interfaces: one in master mode (for fake AP) and second in monitor mode (to listen on).
What is WEP Cracking?
Wired Equivalent Privacy (WEP) is a security algorithm for IEEE 802.11 wireless networks. Introduced as part of the original 802.11 standard ratified in 1997, its intention was to provide data confidentiality comparable to that of a traditional wired network.
It’s fairly easy to crack WEP due to flaws in the algorithm if you are setting up your WiFi network you should opt for WPA.
How to Use the WEP Key Cracker Tool
1. Setup fake AP with KARMA tools or iwconfig
|
1 2 3 4 5 6 |
iwpriv ath0 mode 2 iwconfig ath0 mode master essid foo enc 1122334455 channel 7 echo 1 > /proc/sys/dev/ath0/rawdev echo 1 > /proc/sys/dev/ath0/rawdev_type ifconfig ath0 up ifconfig ath0raw up< |
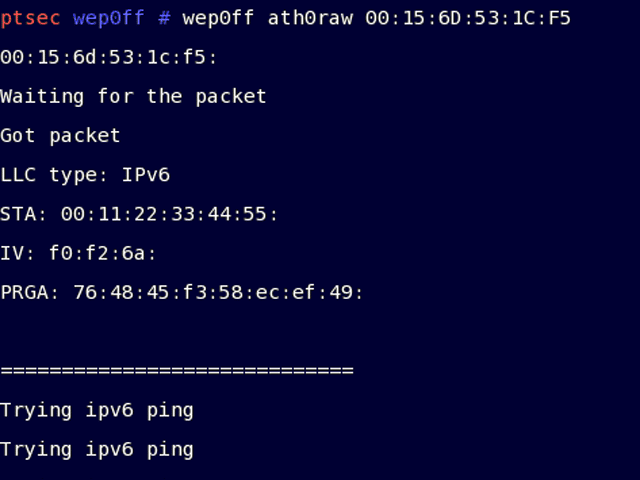
2. Start this program (./wep0ff ath0raw 00:01:02:03:04:05)
3. Wait until client connect to fake access point
4. Launch airodump-ng to collect packets
5. Launch aircrack-ng to recover WEP key
You can download it here:

jimmy says
hi what os is this used on?
Gouki says
GNU/Linux
DotSlashZero says
Can it be used on Cygwin?
i have a fedora in another computer but i’d do better in my laptop in which i only have cygwin… i gess i’d have to install a lot of software huh?
like iwconfig or something?
Darknet says
DotSlashZero: I don’t tend to use tools like this on Cygwin as they require native driver support, which windows doesn’t give. I would suggest setting up a VMWare image of a Linux install or just use a liveCD like Backtrack to access tools like this.
DotSlashZero says
VMWare image of a Linux? is that like a virtual linux within windows? i have a linux version called DSL Damn Small Linux and i think it does that… am i right?
Chris says
What of a Wepkey crack for windows?
yogesh says
good
Hyper says
Does these tools (airodump-ng, KARMA tools or iwconfig,aircrack-ng) work with all wireless cards. Because i have tried some other tools before and had to be atheros wireless card (something like this)
bob says
hey dudes once you have a wep key how do you recover the original password from that
shakezz says
i have a windows vista laptop and no wep hack programs seem to be compatible, can somebody suggest one.
winx says
most tools like this tend to require specific wifi cards (usb afaik just aint good enough) with specific chips atheros and prisim chips are (to my knowledge) the most widely used. look hard enough and you’ll find which ones are compatible with wep cracking tools
sunny says
i want this software comfortabe for win vista and wireless (dell wireless 1395 wlan mini card)
maysiool says
nice and good for everybody
k-ryder says
i have toshiba satellite laptop with Vista premium. will this program work on my pc or do i have to get another cpu like my IBM
wepkey says
hey men so how could we get this baby working im using windows vista your help is much appriciated thankx
navin says
people ought to learn to read!! Dear Mr. wepkey, Wep0ff runs on the Linux OS, and does not run on the Windows Vista OS
As such U need to either, a) install linux on your comp/lappy
b)use a live CD (Backtrack is recommended by most L337 h@xors)
c)Create a virtual drive using a tool like wubi (for ubuntu) on your system and install and run Linux off it
Using these steps you can , as you put it, “get this baby working”
n00b <– That my friend, is a complement of the highest order for people like U!! ;)
Bogwitch says
Heh – I thought all the morons asking for Vista versions were trolling.
That’s the Interwebs for ya!
avinash says
which type of file or softwar .tar
3p1c says
i’ve got a toshiba satellite with a 802.11a/g/n wireless, i been obtaining a few connections locally, i was wondering if you could help :D