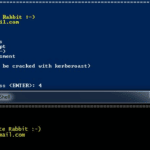
PowerMemory is a PowerShell based tool to exploit Windows credentials present in files and memory, it levers Microsoft signed binaries to hack Windows. The method is totally new. It proves that it can be extremely easy to get credentials or any other information from Windows memory without needing to code in C-type languages. In addition, […]
hacking-windows
Gdog – Python Windows Backdoor With Gmail Command & Control
Gdog is a stealthy Python Windows backdoor that uses Gmail as a command and control server, it’s inspired by Gcat and pushes a little beyond a proof of concept with way more features. And don’t forget, Gcat also inspired Twittor – Backdoor Using Twitter For Command & Control. Features Encrypted transportation messages (AES) + SHA256 […]
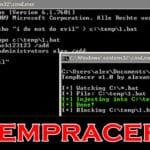
TempRacer – Windows Privilege Escalation Tool
TempRacer is a Windows Privilege Escalation Tool written in C# designed to automate the process of injecting user creation commands into batch files with administrator level privileges. The code itself is not using that many resources because it relies on callbacks from the OS. You can keep it running for the the whole day to […]
Gcat – Python Backdoor Using Gmail For Command & Control
Gcat is a stealthy Python backdoor that uses Gmail as a command and control server. It’s fairly basic right now, but it’s an interesting proof of concept and if the community got behind it and contributed some new features it could be a pretty powerful piece of kit. Feature wise it doesn’t have that much, […]
OAT – Microsoft OCS Assessment Tool (Office Communication Server)
OAT is an Open Source Microsoft OCS Assessment Tool designed to check the password strength of Lync and Microsoft Office Communication Server users. After a password is compromised, OAT demonstrates potential UC attacks that can be performed by legitimate users if proper security controls are not in place. We first wrote about OAT when it […]