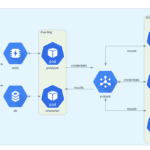
The Trident project is an automated password spraying tool developed to be deployed across multiple cloud providers and provides advanced options around scheduling and IP pooling. trident was designed and built to fulfill several requirements and to provide: the ability to be deployed on several cloud platforms/execution providers the ability to schedule spraying campaigns in […]
Password Cracking Tools
Password cracking and the associated password cracker tools are often the area of information security and hacking that people get most excited about, oh wow I can hack email passwords? We get emails pretty much every day asking how to crack someone's Facebook password, or retrieve website credentials etc.

What is Password Cracking?
As commonly defined:
In cryptanalysis and computer security, password cracking is the process of recovering passwords from data that have been stored in or transmitted by a computer system. A common approach (brute-force attack) is to try guesses repeatedly for the password and check them against an available cryptographic hash of the password.
The purpose of password cracking might be to help a user recover a forgotten password (installing an entirely new password is less of a security risk, but it involves System Administration privileges), to gain unauthorized access to a system, or as a preventive measure by system administrators to check for easily crackable passwords. On a file-by-file basis, password cracking is utilized to gain access to digital evidence for which a judge has allowed access but the particular file's access is restricted.
From Wikipedia.
The Best Password Cracker Software
We have covered many of the most famous, some great examples are:
- Brutus Password Cracker – Download brutus-aet2.zip AET2
- THC-Hydra – The Fast and Flexible Network Login Hacking Tool
- Download pwdump 1.4.2 and fgdump 1.3.4 – Windows Password Dumping
- Cain & Abel – Download the Super Fast and Flexible Password Cracker with Network Sniffing
- JTR (Password Cracking) – John the Ripper 1.7 Released – FINALLY
- Ophcrack 2.2 Password Cracker Released
- hashcat – Multi-Threaded Password Hash Cracking Tool
- Medusa 2.0 Released – Parallel Network Login Brute Forcing Tool
And we have also published some related resources such as:
- Password Cracking Wordlists and Tools for Brute Forcing
- Password Cracking with Rainbowcrack and Rainbow Tables
SharpHose – Asynchronous Password Spraying Tool
SharpHose is an asynchronous password spraying tool in C# for Windows environments that takes into consideration fine-grained password policies and can be run over Cobalt Strike’s execute-assembly. It provides a flexible way to interact with Active Directory using domain-joined and non-joined contexts, while also being able to target specific domains and domain controllers. The tool […]
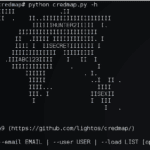
credmap – The Credential Mapper
Credmap is an open source credential mapper tool that was created to bring awareness to the dangers of credential reuse. It is capable of testing supplied user credentials on several known websites to test if the password has been reused on any of these. It is not uncommon for people who are not experts in […]
pemcracker – Tool For Cracking PEM Files
pemcracker is a tool for cracking PEM files that are encrypted and have a password. The purpose is to attempt to recover the password for encrypted PEM files while utilising all the CPU cores. Inspired by Robert Graham’s pemcrack, it still uses high-level OpenSSL calls in order to guess the password. As an optimisation, instead […]
PowerMemory – Exploit Windows Credentials In Memory
PowerMemory is a PowerShell based tool to exploit Windows credentials present in files and memory, it levers Microsoft signed binaries to hack Windows. The method is totally new. It proves that it can be extremely easy to get credentials or any other information from Windows memory without needing to code in C-type languages. In addition, […]