THC Hydra Download below, this software rocks, it’s pretty much the most up to date and currently developed password brute forcing tool around at the moment.
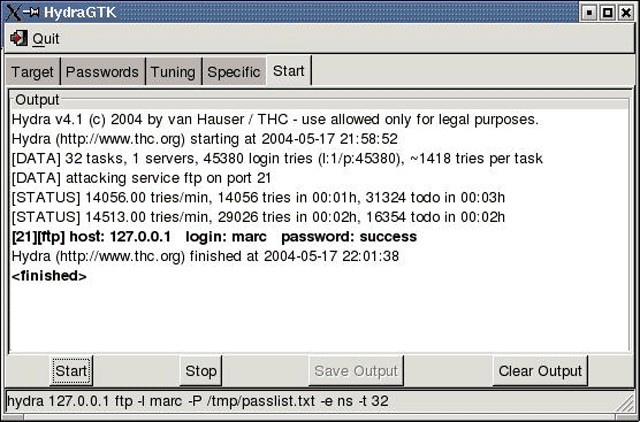
Number one problem with security and people getting hacked are passwords, as every password security study shows. Hydra is a parallelized login cracker which supports numerous protocols to attack. New modules are easy to add, besides that, it is flexible and very fast.
It supports a LOT of services and protocols too.
THC Hydra Hacking Tool Features
There are already several login hacker tools available, however, none does either support more than one protocol to attack or support parallelized connects.
Currently, this tool supports:
- TELNET
- FTP
- HTTP-GET
- HTTP-HEAD
- HTTPS-GET
- HTTP-HEAD
- HTTP-PROXY
- LDAP2
- LADP3
- SMB
- SMBNT
- MS-SQL
- MYSQL
- POSTGRES
- REXEC
- SOCKS5
- VNC
- POP3
- IMAP
- NNTP
- PCNFS
- ICQ
- SAP/R3
- Cisco auth
- Cisco enable
- SMTP-AUTH
- SSH2
- SNMP
- CVS
- Cisco AAA
However, the module engine for new services is very easy so it won’t take a long time until even more services are supported. Planned are: SSH v1, Oracle and more…
This tool is a proof of concept code, to give researchers and security consultants the possibility to show how easy it would be to gain unauthorized access from remote to a system.
Download THC Hydra
You can THC Hydra download is here:
How to install THC Hydra
Compile and install (./configure; make; make install)
If you want the THC Hydra windows hydra.exe version you can grab the Cygwin version from thc.org.
More info is available here

Gouki says
Ubuntu and Debian users have the pre-compiled packages here:
http://blog.goukihq.org/2006/07/28/the-hackers-choice-hydra-on-ubuntu/
Darknet says
Gouki: Thanks that’ll be useful!
matt says
Can someone tell me what i did wrong with the login file? I put hydra -L /matt/documents and setting/logins.txt -Anyone got an example to share or can someone provide some help? Thanks
The Mesterious Stranger says
I need help this wont run and i need a good bruteforcer…When i click on hydra a command prompt shows up then dissapers about .5 seconds later. What am i doing wrong?!?!?!?!?!?!?!??!?!?
richard a says
i’m having the same problem as The Mysterious Stranger above. anybody know what were doing wrong? thanks
onlyforfun says
hello,this is a good site for learing crack, thank you all.
i
backbone says
The Mesterious Stranger
The windows version has maybe no frontend… have you thought about this? the just start you command prompt and run it from there… a list of options should appear…
Crazum says
i ran the command prompt, now what. i typed in ./configure and it says that it is unrecognized or something. please help. thanks.
Maiku says
ummm no exe file?
Pantagruel says
It’s *nix only, so get Cygwin to run it
Maiku says
yeah figured that out a few minutes ago xD thanks!
Alex says
Hello,
i tried to download the hydra-5.3-win.zip on
the THC-Hydra homepage, and my anti virus programm detected
a virus, is this normal for the data??
pls help me!
Bogwitch says
It is very usual for hacking tools to be identified as malware. Considering hacking tools are developed by the hacking community, it would be wise to treat any tool you have acquired with a fair degree of suspicion. If you have the ability, tools and techniques to either examine the source code or monitor what the application is actually doing it would probably be best to avoid attempting to hack altogether until you can.
Additionally, running any hacking tools on your production/ main workstation is a Bad Idea.
Alex says
ok, thx for your advise!
Alex says
now i have another problem,
i downloaded cygwin, wrote the command, but it doesn’t work!
what can i do?
Bogwitch says
You’ll need to give a little more information than that. Any error messages? What do you mean ‘it doesn’t work’?
Alex says
ok, when i write the command, ” no such file or directory” or “Error: Coudn’t find hydra.exe ” appears.
Bogwitch says
OK, which error do you get under which circumstances?
Are you running the command from the directory where you extracted the files?
Is your anti-virus blocking access to the files?
lafluaf says
You have to store the dll files which comes with the zip package in you x:/cygwin/bin folder and then start it with a dos console.
it’s a downgrade of the dll used in general
Alex says
the link to download it does not work. Where can you get a copy of it?
Darknet says
Links updated because you’re too retarded to Google for thc-hydra or just go to the homepage..
bewolf says
i have some probleme:
Checking for SAP/R3 (librfc/saprfc.h) …
… NOT found, module sapr3 disabled
any ideas ?!!
Thk’s
Haxer says
ok heres how u fix in windows version DOWNLOAD WINDOWS VERSION NOT 1 WERE I HAVE TO DO CONFIGURE AND THAT CRUD
Haxer says
kk now u go to start>run type cmd hit enter
now cd to where u put the files in
when ur in folder type this hydra -h now u should see bunch of commands so u type hydra (script here)
jeck says
“coudn
t create signal pipe". whats this?dblackshell says
@jeck: are you running the windows version, or are you running it with cygwin… if the second is the case read the following http://www.cygwin.com/ml/cygwin/2005-02/msg00286.html
T says
I’m confused as to how this program works. Does it enable you to get passwords that have been entered into remote computers?
Casso says
I can’t downlaod the program. Can anyone upload it on megaupload or rapidshare ? thx
I don’t speak english very well
Bogwitch says
@Cosso, if you can’t managee to download the program, you shouldn’t be using it!