Yasca is an open source program which looks for security vulnerabilities, code-quality, performance, and conformance to best practices in program source code. It’s basically a tool-kit for multi-language static analysis.
Yasca can scan source code written in Java, C/C++, HTML, JavaScript, ASP, ColdFusion, PHP, COBOL, .NET, and other languages
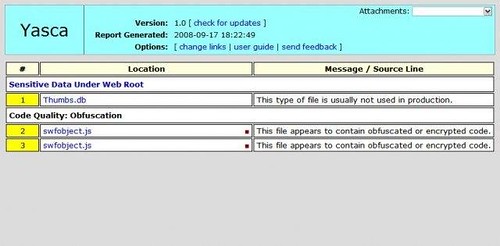
It leverages on external open source programs, such as:
Yasca can be used to scan specific file types, and also contains many custom scanners developed just for it. It is a command-line tool that generates reports in HTML, CSV, XML, SQLite, and other formats. Yasca is easily extensible via a plugin-based architecture, so scanning any particular file is as simple as coming up with the rules or integrating external tools. Yasca also features a simple regular-expression plugin that allows new rules to be written in less than a minute.
Yasca is written in command-line PHP and released under the BSD license.
Usage
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 |
Usage: yasca [options] directory Perform analysis of program source code. --debug additional debugging -h, --help show this help -i, --ignore-ext EXT,EXT ignore these file extensions (default: exe,zip,jpg,gif,png,pdf,class) --ignore-file FILE ignore findings from the specified xml file --source-required only show findings that have source code available -f, --fixes FILE include fixes, written to FILE (default: not included) (EXPERIMENTAL) -s, --silent do not show any output -v, --version show version information Examples: yasca c:\source_code yasca /opt/dev/source_code yasca -o c:\output.csv --report CSVReport "c:\foo bar\quux" |
You can download Yasca here:
Or read more here.
