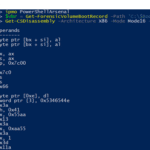
PowerShellArsenal is basically PowerShell for reverse engineering in a module format. The module can be used to disassemble managed and unmanaged code, perform .NET malware analysis, analyse/scrape memory, parse file formats and memory structures, obtain internal system information, etc. PowerShellArsenal is comprised of the following tools: Disassembly – Disassemble native and managed code. MalwareAnalysis – […]
Secure Coding
Secure coding is very important in software development to ensure code security is high using techniques such as static analysis, code auditing and dynamic analysis to ensure safe coding practices are followed.

What Tools can be used for Secure Coding?
There are a variety of tools to ensure code safety, mostly based on source code auditing and static analysis.
The options available really depend on the language being used with some tools focusing on many languages such as Yasca – Multi-Language Static Analysis Toolset or specialist tools focusing on a single language like Brakeman – Static Analysis Rails Security Scanner.
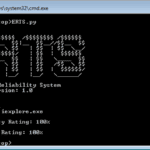
ERTS – Exploit Reliability Testing System
ERTS or Exploit Reliability Testing System is a Python based tool to calculate the reliability of an exploit based on the number of times the exploit is able to control EIP register with the desired address/value. It’s created to help you code reliable exploits and take the manual parts out of running and re-running exploits […]
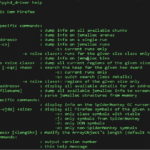
shadow – Firefox Heap Exploitation Tool (jemalloc)
shadow is a new, extended (and renamed version) of a Firefox heap exploitation tool, which is quite a swiss army knife for Firefox/jemalloc heap exploitation. If you want to dive in really deep to this tool, and the technicalities behind it check this out – OR’LYEH? The Shadow over Firefox [PDF] Support shadow has been […]
movfuscator – Compile Into ONLY mov Instructions
The M/o/Vfuscator (short ‘o’, sounds like “mobfuscator”) helps programs compile into only mov instructions, and nothing else – no cheating. Arithmetic, comparisons, jumps, function calls, and everything else a program needs are all performed through mov operations; there is no self-modifying code, no transport-triggered calculation, and no other form of non-mov cheating. The compiler currently […]
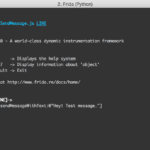
Frida – Dynamic Code Instrumentation Toolkit
Frida is basically Greasemonkey for native apps, or, put in more technical terms, it’s a dynamic code instrumentation toolkit. It lets you inject snippets of JavaScript into native apps on Windows, Mac, Linux, iOS and Android. Frida also provides you with some simple tools built on top of the Frida API. These can be used […]