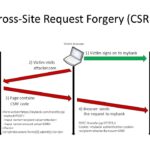
Cross-Site Request Forgery is a term you’ve properly heard in the context of web security or web hacking, but do you really know what it means? The OWASP definition is as follows: Cross-Site Request Forgery (CSRF) is an attack that forces an end user to execute unwanted actions on a web application in which they’re […]
Exploits/Vulnerabilities
Another Week Another Mass Domain Hijacking
Following shortly after the .io domain cock-up that left thousands vulnerable to domain hijacking, this week more than 750 domains were jacked via registrar Gandi. Seems like some pretty sloppy administration going on, but that’s how business goes sadly security is still a very much reactive trade. People don’t enable strict controls and audit unless […]
DJI Firmware Hacking Removes Drone Flight Restrictions
Drones have been taking over the world, everyone with a passing interest in making videos has one and DJI firmware hacking gives you the ability to remove all restrictions (no-fly zones, height and distance) which under most jurisdictions is illegal (mostly EU and FAA for the US). It’s an interesting subject, and also a controversial […]
GnuPG Crypto Library libgcrypt Cracked Via Side-Channel
Some clever boffins including Internet software pioneer djb have gotten libgcrypt cracked via a Side-Channel attack which has to do with the direction of a sliding window carried out in the library. Patches have already been released so update your Linux servers ASAP, even though honestly it seems like a fairly theoretical attack (this side-channel […]
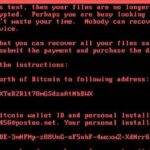
NotPetya Ransomeware Wreaking Havoc
The latest splash has been made by the Petya or NotPetya Ransomware that exploded in Ukraine and is infecting companies all over the World. It’s getting some people in deep trouble as there’s no way to recover the files once encrypted. The malware seems to be trying to hide its intent as it doesn’t really […]