Cross-Site Request Forgery is a term you’ve properly heard in the context of web security or web hacking, but do you really know what it means? The OWASP definition is as follows:
Cross-Site Request Forgery (CSRF) is an attack that forces an end user to execute unwanted actions on a web application in which they’re currently authenticated. CSRF attacks specifically target state-changing requests, not theft of data, since the attacker has no way to see the response to the forged request.
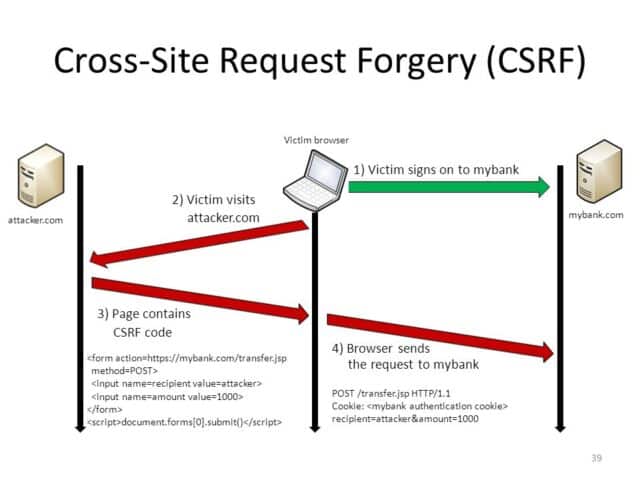
CSRF is often underrated on the risk spectrum but we’ve actually covered some pretty nasty incidents involving CSRF attacks:
– CSRF Vulnerability in Twitter Allows Forced Following
– Password Manager Security – LastPass, RoboForm Etc Are Not That Safe
– Ubiquiti Wi-Fi Gear Hackable Via 1997 PHP Version
And some tools to help test for CSRF vulnerabilities:
– IronWASP – Open Source Web Security Testing Platform
– Hcon Security Testing Framework (HconSTF) v0.4 – Fire Base
– xssless – An Automated XSS Payload Generator Written In Python
Acunetix has come out with a great article explaining it in more depth and also how you can prevent it, it contains information about:
- Cross-site Request Forgery in GET requests
- Cross-site Request Forgery in POST requests
- Preventing CSRF Vulnerabilities
- Anti-CSRF tokens
- Same-site Cookies
For developers, you should pay special attention to the prevention part and make sure whatever you are building is safe.
There are two approaches by which Cross-site Request Forgery (CSRF) may be prevented – synchronizing the Cookie with an anti-CSRF token that has already been provided to the browser, or preventing the browser from sending Cookies to the web application in the first-place.
Check it out in full here: What is Cross-site Request Forgery?

KG says
That’s not much that I need to know, apperently