GetAltName it’s a little script to discover sub-domains that can extract Subject Alt Names for SSL Certificates directly from HTTPS websites which can provide you with DNS names or virtual servers.
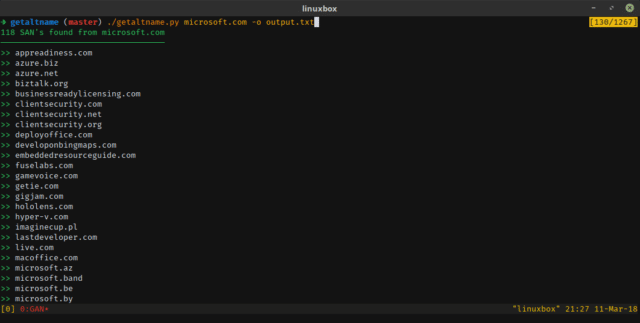
It’s useful in a discovery phase of a pen-testing assessment, this tool can provide you with more information about your target and scope.
Features of GetAltName to Discover Sub-Domains
- Strips wildcards and www’s
- Returns a unique list (no duplicates)
- Works on verified and self-signed certs
- Domain matching system
- Filtering for main domains and TLDs
- Gets additional sub-domains from crt.sh
- Outputs to clipboard
GetAltName Subdomain Exctraction Tool Usage
You can output to a text file and also copy the output to your clipboard as a List or a Single line string, which is useful if you’re trying to make a quick scan with Nmap or other tools.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
usage: getaltname.py [-h] [-p PORT] [-s [timeout]] [-m] [-o OUTPUT] [-c {l,s}] [-d] hostname positional arguments: hostname Host to analyze. optional arguments: -h, --help show this help message and exit -p PORT, --port PORT Destiny port (default 443) -s [timeout], --search-crt [timeout] Retrieve subdomains found in crt.sh -m, --matching-domain Show matching domain name only -o OUTPUT, --output OUTPUT Set output filename -c {l,s}, --clipboard {l,s} Copy the output to the clipboard as a List or a Single string -d, --debug Set debug enable |
GetAltName Required
- colorama
- ndg-httpsclient
- pyperclip
- requests
- tldextract
There are other DNS discovery and extraction tools using different methods, including brute-forcing such as:
– InstaRecon – Automated Subdomain Discovery Tool
– hostmap 0.2 – Automatic Hostname & Virtual Hosts Discovery Tool
– SubBrute – Subdomain Brute-forcing Tool
– altdns – Subdomain Recon Tool With Permutation Generation
You can download GetAltName here:
Or read more here.
