SubBrute is a community driven project with the goal of creating the fastest, and most accurate subdomain brute-forcing tool. Some of the magic behind SubBrute is that it uses open resolvers as a kind of proxy to circumvent DNS rate-limiting. This design also provides a layer of anonymity, as SubBrute does not send traffic directly to the target’s name servers.
There are various other options with similar capabilities, such as:
– InstaRecon – Automated Subdomain Discovery Tool
– dnsmap 0.22 Released – Subdomain Bruteforcing Tool
– DNSenum – Domain Information Gathering Tool
– Complemento v0.6 – ReverseRaider Subdomain Scanner
– DNSRecon – DNS Enumeration Script
– Recon-ng – Web Reconnaissance Framework
Features
- Fast, multi-threaded and comes with more than 2000 high quality nameservers in resolver.txt
- Nameservers are verified when they are needed. A seperate thread is responsible creating a feed of nameservers, and corresponding wildcard blacklist.
- SubBrute is now a DNS spider that recursively crawls enumerated DNS records. This feature boosted *.google.com from 123 to 162 subdomains.
- –type enumerate an arbitrary record type (AAAA, CNAME, SOA, TXT, MX…)
- -s can now read subdomains from result files.
- The subdomains enumerated from previous scans can now be used as input to enumerate other DNS records.
Usage
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 |
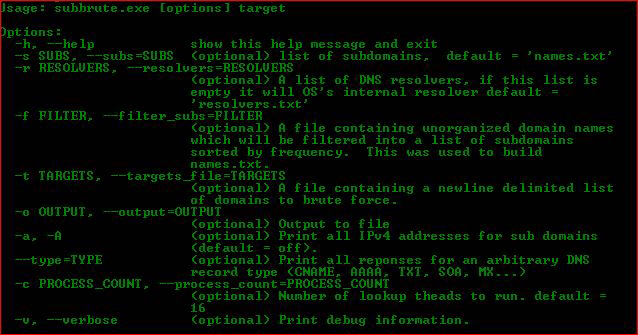
Usage: subbrute.exe [options] target Options: -h, --help show this help message and exit -s SUBS, --subs=SUBS (optional) list of subdomains, default = 'names.txt' -r RESOLVERS, --resolvers=RESOLVERS (optional) A list of DNS resolvers, if this list is empty it will OS's internal resolver default = 'resolvers.txt' -f FILTER, --filter_subs=FILTER (optional) A file containing unorganized domain names which will be filtered into a list of subdomains sorted by frequency. This was used to build names.txt. -t TARGETS, --targets_file=TARGETS (optional) A file containing a newline delimited list of domains to brute force. -o OUTPUT, --output=OUTPUT (optional) Output to file -a, -A (optional) Print all IPv4 addresses for sub domains (default = off). --type=TYPE (optional) Print all reponses for an arbitrary DNS record type (CNAME, AAAA, TXT, SOA, MX...) -c PROCESS_COUNT, --process_count=PROCESS_COUNT (optional) Number of lookup theads to run. default = 16 -v, --verbose (optional) Print debug information. |
You can download SubBrute here:
– subbrute-source-77.zip
– windows-subbrute.zip
Or read more here.

VaxMAN says
The link of the tool in GitHub is incorrectly wrote. The final . (dot) is not needed and the URL don’t work well…
And many thanks for the article/tool!!!
Darknet says
Fixed that, thanks!