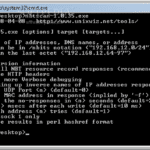
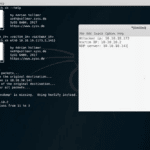
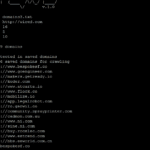
nbtscan is a command-line NetBIOS scanner for Windows that is SUPER fast, it scans for open NetBIOS nameservers on a local or remote TCP/IP network, and this is the first step in the finding of open shares. It is based on the functionality of the standard Windows tool nbtstat, but it operates on a range […]
Archives for September 2017
Equifax Data Breach – Hack Due To Missed Apache Patch
The Equifax data breach is pretty huge with 143 million records leaked from the hack in the US alone with unknown more in Canada and the UK. The original statement about the breach is as follows for those that weren’t up to date with it, which came out Sept 7th (4 months AFTER the breach […]
Seth – RDP Man In The Middle Attack Tool
Seth is an RDP Man In The Middle attack tool written in Python to MiTM RDP connections by attempting to downgrade the connection in order to extract clear text credentials. It was developed to raise awareness and educate about the importance of properly configured RDP connections in the context of pentests, workshops or talks. Usage […]
dcrawl – Web Crawler For Unique Domains
dcrawl is a simple, but smart, multithreaded web crawler for randomly gathering huge lists of unique domain names. How does dcrawl work? dcrawl takes one site URL as input and detects all a href= links in the site’s body. Each found link is put into the queue. Successively, each queued link is crawled in the […]
Time Warner Hacked – AWS Config Exposes 4M Subscribers
What’s the latest on the web, Time Warner Hacked is what it’s about now as a bad AWS S3 config (once again) exposes the details of approximately 4 Million subscribers. This follows not long after the Instagram API leaking user contact information and a few other recent leaks involving poorly secured Amazon AWS S3 buckets […]