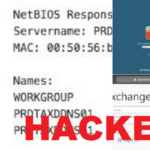
It seems to be non-stop lately, this time it’s Deloitte Hacked, which has also revealed all kinds of publically accessible resources that really should be more secure (VPN, RDP & Proxy services). The irony is that Deloitte positions itself as a global leader in information security and offers consulting services to huge clients all over […]
Archives for September 2017
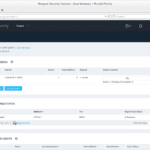
Rapid7 Nexpose Community Edition – Free Vulnerability Scanner
Rapid7 Nexpose Community Edition is a free vulnerability scanner & security risk intelligence solution designed for organizations with large networks, prioritize and manage risk effectively. It proactively supports the entire vulnerability management lifecycle, including discovery, detection, verification, risk classification, impact analysis, reporting and mitigation. Nexpose Community Edition Features Data breaches are growing at an alarming […]
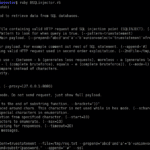
BSQLinjector – Blind SQL Injection Tool Download in Ruby
BSQLinjector is an easy to use Blind SQL Injection tool in Ruby, that uses blind methods to retrieve data from SQL databases. The download is below. The author recommends using the “–test” switch to clearly see how configured payload looks like before sending it to an application. What is Blind SQL Injection? Blind SQL Injection […]
CCleaner Hack – Spreading Malware To Specific Tech Companies
The CCleaner Hack is blowing up, with it initially estimated to be huge, it’s hit at least 700,000 computers and is specifically targeting 20 top tech organisations including Cisco, Intel, Microsoft, Akamai, Samsung and more for a second, more intrusive and pervasive layer of infection. This could be classified as slightly ironic too as CCleaner […]
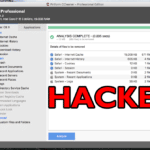
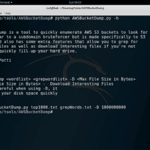
AWSBucketDump – AWS S3 Security Scanning Tool
AWSBucketDump is an AWS S3 Security Scanning Tool, which allows you to quickly enumerate AWS S3 buckets to look for interesting or confidential files. It’s similar to a subdomain brute-forcing tool but is made specifically for S3 buckets and also has some extra features that allow you to grep for delicious files as well as […]