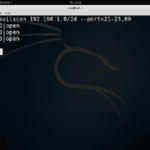
evilscan is a Node.js based massive IP Port scanner designed for concurrency, speed and scanning large ranges of IP addresses. Features Individual IP or IP range scan Individual port, ports list, or port range Banner grabbing (not fully implemented, works with verbose ports only) IAC negotiation Reverse dns Geolocation information Shell or JSON output Optional progress […]
Archives for May 2017
sheep-wolf – Exploit MD5 Collisions For Malware Detection
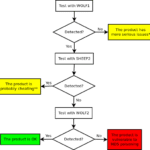
sheep-wolf is a tool to help you Exploit MD5 Collisions in software, specially malware samples which are commonly detected using MD5 hash signatures. and then a malicious one (Wolf) that have the same MD5 hash. Please use this code to test if the security products in your reach use MD5 internally to fingerprint binaries and […]
Massive Acunetix Online Update Brings New Features & UI
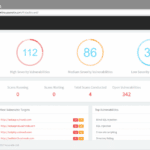
So there’s been a massive Acunetix Online update that has pushed out a brand new UI plus a whole bunch of new features and capabilities, including really powerful stuff for security professionals and organisations who take their security seriously The update has focused a lot on Usability of the UI and features for infosec pros […]
Sn1per – Penetration Testing Automation Scanner
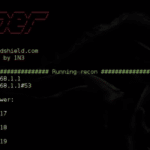
Sn1per is a penetration testing automation scanner that can be used during a penetration test to enumerate and scan for vulnerabilities. Features Automatically collects basic recon (ie. whois, ping, DNS, etc.) Automatically launches Google hacking queries against a target domain Automatically enumerates open ports via NMap port scanning Automatically brute forces sub-domains, gathers DNS info […]
Pybelt – The Hackers Tool Belt
Pybelt is a Python-based hackers tool belt capable of cracking hashes without prior knowledge of the algorithm, scanning ports on a given host, searching for SQLi vulnerabilities in a given URL, verifying that your Google dorks work like they should, verifying the algorithm of a given hash, scanning a URL for XSS vulnerability, and finding […]