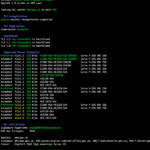
sslscan is a very efficient C program that allows you to detect SSL versions & cipher suites (including TLS version checker) and also checks for vulnerabilities like Heartbleed and POODLE. A useful tool to keep around after you’ve set-up a server to check the SSL configuration is robust. Especially if you’re in an Internet limited […]
Archives for December 2016
Malware Writers Using Exclusion Lists To Linger
It seems malware writers using exclusion lists is not something new, but it’s still concerning people. To me it’d be a pretty obvious avenue, especially if you were crafting something a little more nefarious than average – like APT malware (Advanced Persistent Threat) tools. Definitely a chicken and egg problem, especially with Windows if you […]
Minion – Mozilla Security Testing Framework
Minion is a security testing framework built by Mozilla to bridge the gap between developers and security testers. To do so, it enables developers to scan with a wide variety of security tools, using a simple HTML-based interface. It consists of three umbrella projects: Minion Frontend, a Python, angular.js, and Bootstrap-based website that provides a […]
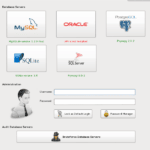
HexorBase – Administer & Audit Multiple Database Servers
HexorBase is a database application designed to administer and to audit multiple database servers simultaneously from a centralised location, it is capable of performing SQL queries and brute-force attacks against common database servers (MySQL, SQLite, Microsoft SQL Server, Oracle, PostgreSQL). It allows packet routing through proxies or even Metasploit pivoting antics to communicate with remotely […]
UK Encryption Backdoor Law Passed Via Investigatory Powers Act
The latest news out of my homeland is not good, the UK encryption backdoor law passed via Investigatory Powers Act or the IPA Bill as it’s commonly known. And itself was passed through a kind of backdoor route, which avoided the scorn of the public. Which was good for the lawmakers, but not for the […]