The latest news out of my homeland is not good, the UK encryption backdoor law passed via Investigatory Powers Act or the IPA Bill as it’s commonly known. And itself was passed through a kind of backdoor route, which avoided the scorn of the public.
Which was good for the lawmakers, but not for the citizens as with the case of the Burr-Feinstein Bill proposed in the US which was turned around by a huge backlash.
Among the many unpleasant things in the Investigatory Powers Act that was officially signed into law this week, one that has not gained as much attention is the apparent ability for the UK government to undermine encryption and demand surveillance backdoors.
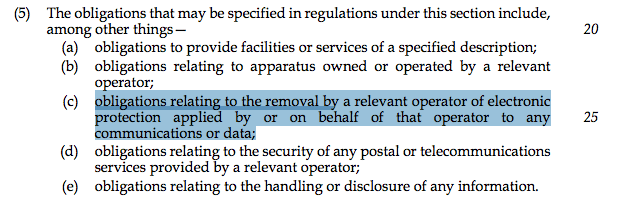
As the bill was passing through Parliament, several organizations noted their alarm at section 217 which obliged ISPs, telcos and other communications providers to let the government know in advance of any new products and services being deployed and allow the government to demand “technical” changes to software and systems.
As per the final wording of the law, comms providers on the receiving end of a “technical capacity notice” will be obliged to do various things on demand for government snoops – such as disclosing details of any system upgrades and removing “electronic protection” on encrypted communications.
There is no point at which forcing companies or service providers to develop or utilise less secure products is a good idea. That’s the problem when policy makers have no real depth in their understanding of the subject and how dangerous the decisions they are making really are.
So now browsing logs are available to the UK government and any form of encryption will be backdoored to allow the government to decrypt it if they feel like it. Great.
Thus, by “technical capability,” the government really means backdoors and deliberate security weaknesses so citizens’ encrypted online activities can be intercepted, deciphered and monitored.
In effect, the UK government has written into law a version of the much-derided Burr-Feinstein Bill proposed in the US, which would have undermined encryption in America. A backlash derailed that draft law.
No such backlash happened in the UK over the Investigatory Powers Bill, though, and so here we are. Web browser histories logged by ISPs 24/7, and the looming possibility of crippled cryptography. There may be not much point using a VPN to conceal your web activities if it can be blown open by a technical capability notice.
To be fair, there were some fears that Blighty’s law would effectively kill off the UK software industry as well as undermine Brits’ privacy, and expose them to surveillance and hacking by criminals exploiting these mandatory backdoors. This mild panic did bring about some changes to the UK’s Investigatory Powers Bill before it was passed.
Next UK will finally be introducing a mandatory ID system scheme, seen as though soon enough everyone will be linked to every transaction they conduct online, on their smart phone or on their TV.
It’s really turning into a draconian state.
Source: The Register

XYZ says
Orwell was right
Freestyler says
Right idea wrong year.