Project Wycheproof is a tool to test crypto libraries against known attacks. It is developed and maintained by members of Google Security Team, but it is not an official Google product. At Google, they rely on many third party cryptographic software libraries. Unfortunately, in cryptography, subtle mistakes can have catastrophic consequences, and they found that […]
Archives for December 2016
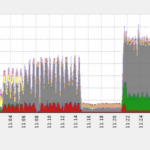
Ending The Year With A 650Gbps DDoS Attack
It seems that 2016 has been the year of immense DDoS attacks, many coming from Mirai. This seems to be a newcomer though ending the year with a 650Gbps DDoS attack. The Dyn DNS DDoS attack that some speculated reached over 1Tbps was probably the biggest, but this isn’t that far behind and it’s bigger […]
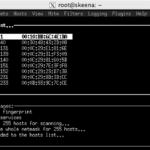
Ettercap – A Suite For Man-In-The-Middle Attacks
Ettercap is a comprehensive suite for man-in-the-middle attacks (MiTM). It features sniffing of live connections, content filtering on the fly and many other interesting tricks. It also supports active and passive dissection of many protocols and includes many features for network and host analysis. Ettercap works by putting the network interface into promiscuous mode and […]
Merry Christmas & A Happy New Year 2017
Wishing you all happy holidays, a Merry Christmas and a Happy New Year 2017 – enjoy the gift of giving. Be jolly, merry and don’t DDoS the PSN Network, or Steam or XBox.. We need our gaming! Have a great one – love Darknet.
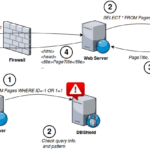
DBShield – Go Based Database Firewall
DBShield is a Database Firewall written in Go that has protection for MySQL/MariaDB, Oracle and PostgreSQL databases. It works in a proxy fashion inspecting traffic and dropping abnormal queries after a learning period to populate the internal database with regular queries. Learning mode lets any query pass but it records information about it (pattern, username, […]