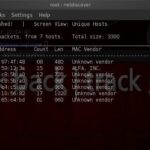
Netdiscover is a network address discovery tool that was developed mainly for those wireless networks without DHCP servers, though it also works on wired networks. It sends ARP requests and sniffs for replies. Built on top of libnet and libpcap, it can passively detect on-line hosts, or search for them, by actively sending ARP requests, […]
Archives for November 2016
Signal Messaging App Formal Audit Results Are Good
I’ve recommended Signal Messaging App quite a few times and I do use it myself, I know there are some privacy concerns with the fact it requires Google App Store – but that’s the developers choice. It’s a pretty solid app, clean, sleek and works well across both Android and iOS and the latest news […]
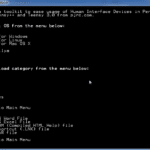
Kautilya – Human Interface Device Hacking Toolkit
Kautilya is a human interface device hacking toolkit which provides various payloads for HIDs which may help with breaking into a computer during penetration tests. The Windows payloads and modules are written mostly in powershell (in combination with native commands) and are tested on Windows 7 and Windows 8. In principal Kautilya should work with […]
Censys Search Engine – Public Host & Network Search
Censys Search Engine is a public host & network search tool that allows computer scientists to ask questions about the devices and networks that compose the Internet. Driven by Internet-wide scanning, it lets researchers find specific hosts with the networksearch and create aggregate reports on how devices, websites, and certificates are configured and deployed. Censys […]
UK Teen Earned More Than US$385,000 From DDoS Service
Another DDoS service down after the owner got busted, this time a UK teenager who created the service called Titanium Stresser when he was just 15. Not long ago we wrote about the two Israeli guys who got busted for running the VDoS-s.com DDoS Service. There seems to be a bit of a crack down […]