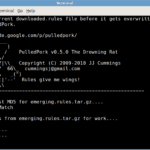
Pulled Pork is a PERL based tool for Suricata and Snort rule management – it can determine your version of Snort and automatically download the latest rules for you. The name was chosen because simply speaking, it Pulls the rules. Using a regular crontab you can keep your Snort or Suricata rules up to date […]
Archives for November 2016
Acunetix Web Vulnerability Scanner v11 Released
Acunetix Web Vulnerability Scanner v11 has just been released with lots of exciting new features and tools. The biggest change is that v11 is now integrated with Vulnerability Management features to enable your organization to comprehensively manage, prioritise and control vulnerability threats – ordered by business criticality. There are other changes too including the web […]
PyExfil – Python Data Exfiltration Tools
PyExfil started as a Proof of Concept (PoC) and has ended up turning into a Python Data Exfiltration toolkit, which can execute various techniques based around commonly allowed protocols (HTTP, ICMP, DNS etc). The package is very early stage (alpha release) so is not fully tested, any feedback and commits are welcomed by the author. […]
Androguard – Reverse Engineering & Malware Analysis For Android
Androguard is a toolkit built in Python which provides reverse engineering and malware analysis for Android. It’s buyilt to examine * Dex/Odex (Dalvik virtual machine) (.dex) (disassemble, decompilation), * APK (Android application) (.apk), * Android’s binary xml (.xml) and * Android Resources (.arsc). Androguard is available for Linux/OSX/Windows (Python powered). Features Map and manipulate DEX/ODEX/APK/AXML/ARSC […]
Android Devices Phoning Home To China
So unsurprisingly a security researcher found some cheap Android devices phoning home to China when buying a phone to travel with. One of the phones seems to be Blu R1 HD, which is ‘Currently unavailable’ on Amazon.com and customers that bought it have received security update e-mails. Security researchers have uncovered a secret backdoor in […]