Scallion is a GPU-driven Onion Hash Generator written in C#, it lets you create vanity GPG keys and .onion addresses (for Tor’s hidden services) using OpenCL. Scallion runs on Mono (tested in Arch Linux) and .NET 3.5+ (tested on Windows 7 and Server 2008) Scallion was used to find collisions for every 32bit key id […]
Cryptography
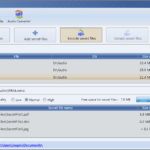
DeepSound – Audio Steganography Tool
DeepSound is an audio steganography tool and audio converter that hides secret data into audio files, the application also enables you to extract secret files directly from audio files or audio CD tracks. This audio steganography tool can be used as copyright marking software for wave, flac, wma, ape, and audio CD. DeepSound also support […]
libsodium – Easy-to-use Software Library For Encryption
Sodium is a new, easy-to-use software library for encryption, decryption, signatures, password hashing and more. It is a portable, cross-compilable, installable, packageable fork of NaCl, with a compatible API, and an extended API to improve usability even further. Its goal is to provide all of the core operations needed to build higher-level cryptographic tools. Sodium […]
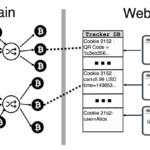
Bitcoin Anonymity Compromised By Most Vendors
Cryptocurrency is getting a lot of press lately and some researchers dug a little bit deeper in Bitcoin anonymity as it’s a touted selling point for most cryptocurrencies. It’s not a problem with Bitcoin itself, or any other coin, more the fact that shopping cart implementations and analytics systems aren’t built with the anonymity of […]
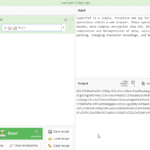
CyberChef – Cyber Swiss Army Knife
CyberChef is a simple, intuitive web app for carrying out all manner of “cyber” operations within a web browser. These operations include simple encoding like XOR or Base64, more complex encryption like AES, DES and Blowfish, creating binary and hexdumps, compression and decompression of data, calculating hashes and checksums, IPv6 and X.509 parsing, changing character […]