Pybelt is a Python-based hackers tool belt capable of cracking hashes without prior knowledge of the algorithm, scanning ports on a given host, searching for SQLi vulnerabilities in a given URL, verifying that your Google dorks work like they should, verifying the algorithm of a given hash, scanning a URL for XSS vulnerability, and finding […]
Cryptography
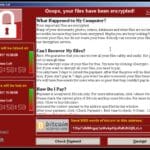
WannaCry Ransomware Foiled By Domain Killswitch
Whilst I was away on a tropical island enjoying myself the Infosec Internet was on fire with news of the global WannaCry ransomware threat which showed up in the UK NHS and was spreading across 74 different countries. The Ransomware seems to be the first that is P2P using an SMB exploit from the NSA […]
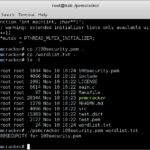
pemcracker – Tool For Cracking PEM Files
pemcracker is a tool for cracking PEM files that are encrypted and have a password. The purpose is to attempt to recover the password for encrypted PEM files while utilising all the CPU cores. Inspired by Robert Graham’s pemcrack, it still uses high-level OpenSSL calls in order to guess the password. As an optimisation, instead […]
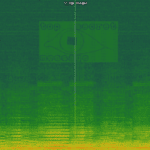
spectrology – Basic Audio Steganography Tool
spectrology is a Python-based audio steganography tool that can convert images to audio files with a corresponding spectrogram encoding, this allows you to hide hidden messages via images inside audio files. Using this tool you can select range of frequencies to be used and all popular image codecs are supported. Usage
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 |
usage: spectrology.py [-h] [-o OUTPUT] [-b BOTTOM] [-t TOP] [-p PIXELS] [-s SAMPLING] INPUT positional arguments: INPUT Name of the image to be converted. optional arguments: -h, --help show this help message and exit -o OUTPUT, --output OUTPUT Name of the output wav file. Default value: out.wav). -b BOTTOM, --bottom BOTTOM Bottom frequency range. Default value: 200. -t TOP, --top TOP Top frequency range. Default value: 20000. -p PIXELS, --pixels PIXELS Pixels per second. Default value: 30. -s SAMPLING, --sampling SAMPLING Sampling rate. Default value: 44100. |
Example
|
1 |
python spectrology.py test.bmp -b 13000 -t 19000 |
You […]
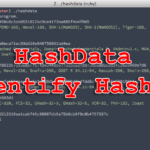
HashData – A Command-line Hash Identifying Tool
HashData is a Ruby-based command-line REPL Hash Identifying Tool with support for a lot of different (most popular) hash types. Installation
|
1 |
$ gem install hashdata |
Usage Command Line When installed, run hashdata and paste in hashes when prompted. Library Example Script:
|
1 2 3 |
require 'hashdata' hash = HashData.new puts(hash.check_type("1111111111111",'DES')) |
The above should output true. The library only matches the start of your second input, this […]