Some clever boffins including Internet software pioneer djb have gotten libgcrypt cracked via a Side-Channel attack which has to do with the direction of a sliding window carried out in the library. Patches have already been released so update your Linux servers ASAP, even though honestly it seems like a fairly theoretical attack (this side-channel […]
Cryptography
OpenPuff – Professional Steganography Tool
OpenPuff is a professional steganography tool, with unique features you won’t find among any other free or commercial software. OpenPuff is 100% free and suitable for highly sensitive data covert transmission. The tool contains deniable steganography, carrier chains, unique layers of security and obfuscation, multiple carrier formats, is portable and is freeware (ad-free). Features of […]
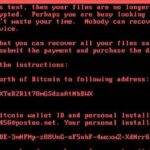
NotPetya Ransomeware Wreaking Havoc
The latest splash has been made by the Petya or NotPetya Ransomware that exploded in Ukraine and is infecting companies all over the World. It’s getting some people in deep trouble as there’s no way to recover the files once encrypted. The malware seems to be trying to hide its intent as it doesn’t really […]
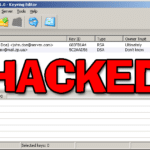
OneLogin Hack – Encrypted Data Compromised
The OneLogin hack is blowing up now it seems like whoever got access can also decrypt encrypted customer data which is just about AS BAD as it can get for a password/identity management service. Now I’m a HUGE supporter of password management tools as I’ve mentioned many times here, so anyone who signed up for […]
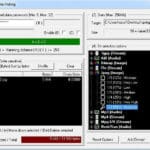
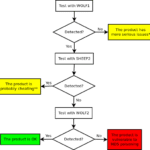
sheep-wolf – Exploit MD5 Collisions For Malware Detection
sheep-wolf is a tool to help you Exploit MD5 Collisions in software, specially malware samples which are commonly detected using MD5 hash signatures. and then a malicious one (Wolf) that have the same MD5 hash. Please use this code to test if the security products in your reach use MD5 internally to fingerprint binaries and […]