CTFR is a Python-based tool to Abuse Certificate Transparency Logs to get subdomains from a HTTPS website in a few seconds.
You missed AXFR technique didn’t you? (Open DNS zone transfers), so how does it work? CTFR does not use dictionary attack or brute-force attacks, it just helps you to abuse Certificate Transparency Logs.
What is Certificate Transparency?
Google’s Certificate Transparency project fixes several structural flaws in the SSL certificate system, which is the main cryptographic system that underlies all HTTPS connections. These flaws weaken the reliability and effectiveness of encrypted Internet connections and can compromise critical TLS/SSL mechanisms, including domain validation, end-to-end encryption, and the chains of trust set up by certificate authorities. If left unchecked, these flaws can facilitate a wide range of security attacks, such as website spoofing, server impersonation, and man-in-the-middle attacks.
From: http://www.certificate-transparency.org/
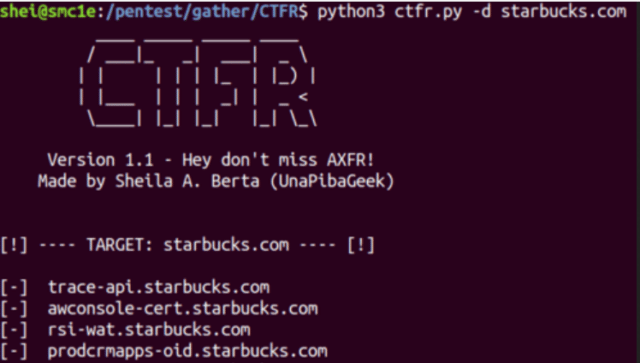
Usage of CTFR to Abuse Certificate Transparency Logs
|
1 2 3 |
$ python3 ctfr.py --help -d --domain [target_domain] (required) -o --output [output_file] (optional) |
Example:
|
1 |
$ python3 ctfr.py -d facebook.com -o /home/shei/subdomains_fb.txt |
This is quite a new and novel technique compared to more traditional scripts like DNSRecon – DNS Enumeration Script.
You can download CTFR here:
Or read more here.
