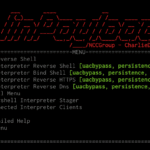
Winpayloads is a tool to provide undetectable Windows payload generation with some extras running on Python 2.7. It provides persistence, privilege escalation, shellcode invocation and much more. The tool uses metasploits meterpreter shellcode, injects the users IP and port into the shellcode and writes a python file that executes the shellcode using ctypes. This is […]
post exploitation
mimikittenz – Extract Plain-Text Passwords From Memory
mimikittenz is a post-exploitation powershell tool that utilizes the Windows function ReadProcessMemory() in order to extract plain-text passwords from various target processes. The aim of mimikittenz is to provide user-level (non-admin privileged) sensitive data extraction in order to maximise post exploitation efforts and increase value of information gathered per target. NOTE: This tool is targeting […]
PowerOPS – PowerShell Runspace Portable Post Exploitation Tool
PowerShell Runspace Portable Post Exploitation Tool aimed at making Penetration Testing with PowerShell “easier”. PowerOPS is an application written in C# that does not rely on powershell.exe but runs PowerShell commands and functions within a powershell runspace environment (.NET). It intends to include multiple offensive PowerShell modules to make the process of Post Exploitation easier. […]
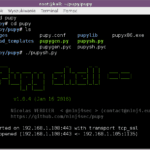
Pupy Download – Open-Source Remote Administration Tool – RAT
Pupy is an open-source remote administration tool (RAT), that is cross-platform and has an embedded Python interpreter, allowing its modules to load Python packages from memory and transparently access remote Python objects. Pupy can communicate using different transports and have a bunch of cool features & modules. On Windows, Pupy uses reflective dll injection and […]