PowerShell Runspace Portable Post Exploitation Tool aimed at making Penetration Testing with PowerShell “easier”. PowerOPS is an application written in C# that does not rely on powershell.exe but runs PowerShell commands and functions within a powershell runspace environment (.NET). It intends to include multiple offensive PowerShell modules to make the process of Post Exploitation easier.
It tries to follow the KISS principle, being as simple as possible. The main goal is to make it easy to use PowerShell offensively and help to evade antivirus and other mitigations solutions. It does this by:
- Doesn’t rely on powershell.exe, it calls PowerShell directly through the .NET framework, which might help bypassing security controls like GPO, SRP and App Locker.
- The payloads are executed from memory and never touch disk, evading most antivirus engines.
Since PowerOPS offers basically an interactive PowerShell command prompt you are free to use the PowerShell tools included the way you want, and additionally execute any valid PowerShell command.
What’s Inside The Runspace
- PowerShellMafia/Powersploit
- Get-Keystrokes
- Invoke-DllInjection
- Invoke-Mimikatz
- Invoke-NinjaCopy
- Invoke-Shellcode
- Invoke-ReflectivePEInjection
- Invoke-TokenManipulation
- Invoke-WMICommand
- PowerUp
- PowerView
- Nishang
- Get-Information
- Get-PassHashes
- Port-Scan
- Auto-GPPPassword
- PowerCat
- Empire
- Invoke-Psexec
- Invoke-SSHCommand
- mimikittenz
- SMBAutoBrute
- PowerUpSQL
Additionally you can run any valid PowerShell command.
Powershell functions within the Runspace are loaded in memory from Base64 Encoded Strings.
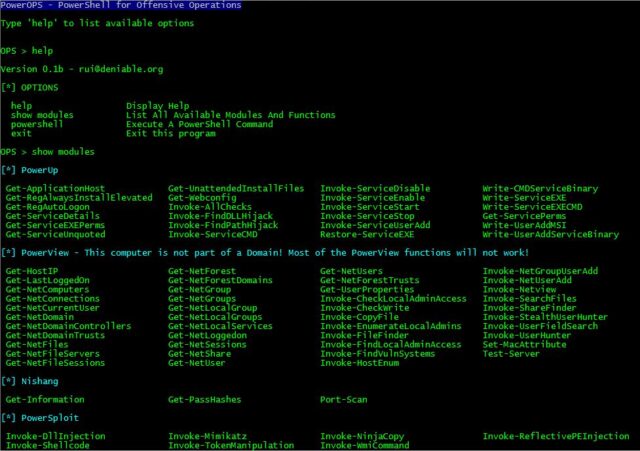
Usage
Just run the binary and type ‘show’ to list available modules.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 |
PS > show [-] This computer is not part of a Domain! Some functions will not work! [+] Nishang Get-Information Get-PassHashes Port-Scan [+] PowerSploit Get-KeyStrokes Invoke-DllInjection Invoke-Mimikatz Invoke-NinjaCopy Invoke-Shellcode Invoke-TokenManipulation Invoke-WmiCommand Invoke-ReflectivePEInjection PowerView PowerUp [+] Empire Invoke-PsExec Invoke-SSHCommand [+] Others Auto-GPPPassword Invoke-SMBAutoBrute Invoke-mimikittenz PowerCat PowerUpSQL PS > |
You can download PowerOPS here:
Or read more here.
