Memhunter is an Automated Memory Resident Malware Detection tool for the hunting of memory resident malware at scale, improving the threat hunter analysis process and remediation times.
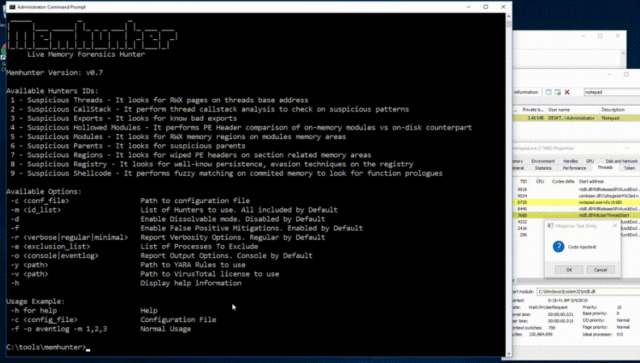
It’s a self contained binary that can be deployed and managed at scale, does not use memory dumps and relies purely on memory inspection to do its work. It also does not require any complex infrastructure to deploy.
The tool was designed as a replacement of memory forensic volatility plugins such as malfind and hollowfind. The idea of not requiring memory dumps helps on performing the memory resident malware threat hunting at scale, without manual analysis, and without the complex infrastructure needed to move dumps to forensic environments.
Memhunter in a nutshell:
- It is an standalone binary that gets itself deployed as a windows service
- It uses a set of memory inspection heuristics and ETW data collection to find footprints left by common injection techniques.
- Forensic information on findings gets reported through console or event logs for forwarding
Memhunter Automated Memory Resident Malware Detection Features
The detection process is performed through a combination of endpoint data collection and memory inspection scanners. The tool is a standalone binary that, upon execution, deploys itself as a windows service. Once running as a service, memhunter starts the collection of ETW events that might indicate code injection attacks. The live stream of collected data events is feed into memory inspection scanners that use detection heuristics to down select the potential attacks. The entire detection process does not require human intervention, neither memory dumps, and it can be performed by the tool itself at scale.
- 9 hunter heuristics included (see next slide)
- 15 code injection techniques implemented on minjector test tool
- ETW data collection of suspicious events used for heuristic triggering
- Windows Event Log generation
- Exclusion of baseline detection
- Basic forensic information
- Sqlite storage integration
Memhunter Automated Memory Resident Malware Detection minjector.exe
Besides the data collection and hunting heuristics, the project has also led to the creation of a companion tool called “minjector” that contains +15 code injection techniques. The minjector tool cannot only be used to exercise memhunter detections, but also as a one-stop location to learn on well-known code injection techniques out there.
You can download Memhunter here:
Or read more here.

Sajid al orchid says
I want hacking education
Memespeak says
If you don\’t mind importing unknown/foriegn libraries blindly, go for it.
Darknet says
The code is all public on Github, feel free to actually get to know the code and what it does vs whinging.