Androguard is a toolkit built in Python which provides reverse engineering and malware analysis for Android.
It’s buyilt to examine * Dex/Odex (Dalvik virtual machine) (.dex) (disassemble, decompilation), * APK (Android application) (.apk), * Android’s binary xml (.xml) and * Android Resources (.arsc).
Androguard is available for Linux/OSX/Windows (Python powered).
Features
- Map and manipulate DEX/ODEX/APK/AXML/ARSC format into full Python objects
- Diassemble/Decompilation/Modification of DEX/ODEX/APK format
- Decompilation with the first native (directly from dalvik bytecodes to java source codes) dalvik decompiler (DAD)
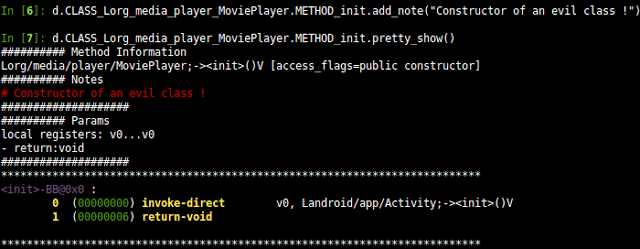
- Access to the static analysis of the code (basic blocks, instructions, permissions)
- Analysis a bunch of android apps
- Analysis with ipython/Sublime Text Editor
- Diffing of android applications
- Measure the efficiency of obfuscators (proguard, …)
- Determine if your application has been pirated (plagiarism/similarities/rip-off indicator)
- Check if an android application is present in a database (malwares, goodwares ?)
- Open source database of android malware
- Detection of ad/open source librairies (WIP)
- Risk indicator of malicious application
- Reverse engineering of applications (goodwares, malwares)
- Transform Android’s binary xml (like AndroidManifest.xml) into classic xml
- Visualize your application with gephi (gexf format), or with cytoscape (xgmml format), or PNG/DOT output
- Integration with external decompilers (JAD+dex2jar/DED/fernflower/jd-gui…)
Usage
Androguard has many different components, but the most commonly used one would be Androlyze:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
Usage: androlyze.py [options] Options: -h, --help show this help message and exit -i INPUT, --input=INPUT file : use this filename -d, --display display the file in human readable format -m METHOD, --method=METHOD display method(s) respect with a regexp -f FIELD, --field=FIELD display field(s) respect with a regexp -s, --shell open a shell to interact more easily with objects -v, --version version of the API -p, --pretty pretty print ! -t TYPE_PRETTY, --type_pretty=TYPE_PRETTY set the type of pretty print (0, 1) ! -x, --xpermissions show paths of permissions |
You can download Androguard here:
Or read more here.
