SNIFFlab is a set of scripts in Python that enable you to create your own MITM test environment for packet sniffing through a WiFi access point.
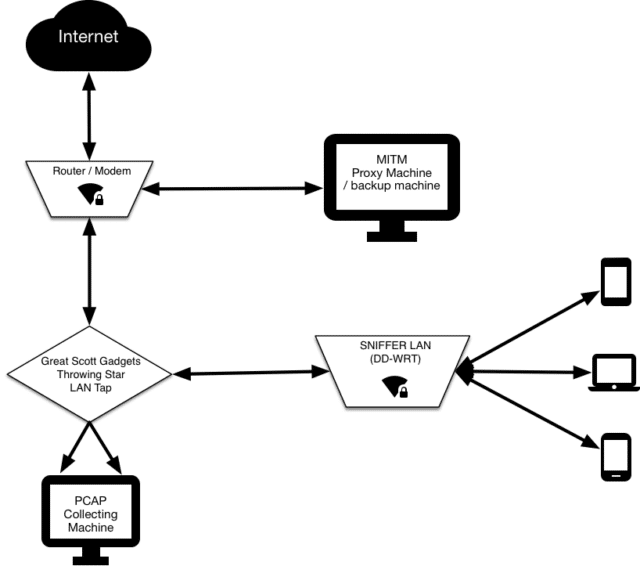
Essentially it’s a WiFi hotspot that is continually collecting all the packets transmitted across it. All connected clients’ HTTPS communications are subjected to a “Man-in-the-middle” attack, whereby they can later be decrypted for analysis
What is SNIFFLab MITM Test Environment
In our environment, dubbed Snifflab, a researcher simply connects to the Snifflab WiFi network, is prompted to install a custom certificate authority on the device, and then can use their device as needed for the test.
All traffic on the network is logged by a Raspberry Pi dedicated to that task. The traffic is cloned by a Great Scott Gadgets Throwing Star LAN Tap, which routes it both to its destination, and to our Raspberry Pi. The Pi continually collects packet data, creating new packet capture (pcap) files at a regular interval, or once the active file reaches a configurable size. Saved files are regularly transferred to another machine for persistent storage. Users with SSH access to the Pi can also manually restart the pcap service, to get instant access to the captured packets, instead of waiting for the interval.
The custom certificate that each client must install enables the proxy server through which SNIFFlab routes its traffic to intercept HTTPS requests to the outside world, and re-encrypt them using certificates generated on-the-fly. This allows for the researcher to later decrypt most captured network traffic sent over HTTPS.
Using SNIFFLab MITM Enivronment
|
1 2 3 4 5 6 7 8 |
SNIFFlab.py -h -i (specify the network interface) -s (specify the file size limit) -t (specify the time interval, in seconds, between new PCAP files) -f (specify a filename suffix to append to each PCAP. -u (specify a ssh username for a remote backup) -h (specify a ssh host for remote backup) -p (specify the path on the remote host for backup) |
There are some other related tools here:
– mitmproxy – Intercepting HTTP Proxy Tool aka MITM
– MANA Toolkit – Rogue Access Point (evilAP) And MiTM Attack Tool
– BetterCap – Modular, Portable MiTM Framework
– MITMf – Man-In-The-Middle Attack Tool
You can download SNIFFlab here:
Or read more here.
