Whilst I was away on a tropical island enjoying myself the Infosec Internet was on fire with news of the global WannaCry ransomware threat which showed up in the UK NHS and was spreading across 74 different countries.
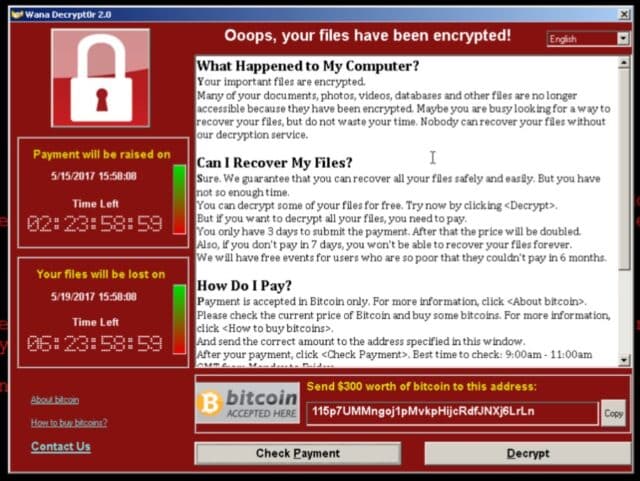
The Ransomware seems to be the first that is P2P using an SMB exploit from the NSA Leak just last month.
The WannaCrypt ransomware worm, aka WanaCrypt or Wcry, today exploded across 74 countries, infecting hospitals, businesses including Fedex, rail stations, universities, at least one national telco, and more organizations.
In response, Microsoft has released emergency security patches to defend against the malware for unsupported versions of Windows, such as XP and Server 2003, as well as modern builds.
To recap, WannaCrypt is installed on vulnerable Windows computers by a worm that spreads across networks by exploiting a vulnerability in Microsoft’s SMB file-sharing services. It specifically abuses a bug designated MS17-010 that Redmond patched in March for modern versions of Windows, and today for legacy versions – all remaining unpatched systems are therefore vulnerable and can be attacked.
This bug was, once upon a time, exploited by the NSA to hijack and spy on its targets. Its internal tool to do this, codenamed Eternalblue, was stolen from the agency, and leaked online in April – putting this US government cyber-weapon into the hands of any willing miscreant. Almost immediately, it was used to hijack thousands of machines on the internet.
Now someone has taken that tool and strapped it to ransomware: the result is a variant of WannaCrypt, which spreads via SMB and, after landing on a computer, encrypts as many files as it can find. It charges $300 or $600 in Bitcoin to restore the documents. It is adept at bringing offices and homes to a halt by locking away their data.
There appeared to be over 100,000 infected hosts and quite a number paid netting the attackers over $25,000 (not that great a payday considering how much media coverage it got).
Also, in a very unusual move Microsoft has released patches for all versions of Windows (including all the way back to XP) for the SMB exploit used in the malware. Not that I expect most people getting hammered by it to be installed patches, or blocking access to port 445 over the Internet..or anything else remotely sensible.
And it installs Doublepulsar, a backdoor that allows the machine to be remotely controlled. That’s another stolen NSA tool leaked alongside Eternalblue. The malware is also controlled via the anonymizing Tor network by connecting to hidden services to receive further commands from its masters.
Fortunately, a kill switch was included in the code. When it detects that a particular web domain exists, it stops further infections. That domain was created earlier today by a UK infosec bod, who spotted the dot-com in the reverse-engineered binary; that registration was detected by the ransomware, which immediately halted its worldwide spread.
Connections to the magic domain – iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com – were sinkholed to a server in California, and the admins of infected systems reaching out to the dot-com will be notified, we’re told. “IP addresses from our sinkhole have been sent to FBI and ShadowServer so affected organisations should get a notification soon,” said the researcher. The infosec bod admitted they registered the domain first, then realized it was a kill switch. Still, job done.
The most interesting part for me was when a Malware researched accidentally disabled the spread of the ransomeware by registered a domain it used as a killswitch.
How to Accidentally Stop a Global Cyber Attacks
To be fair, calling it accidental is pretty humble, but he didn’t mean to disable the spread. The malware checked an unregistered domain to see if it resolved, if it did it exited as it most likely means it’s running in a sandbox and being examined or reverse engineered.
The problem was, this guy registered the domain, so after propagation it always resolved, meaning any new instances of WannaCry failed.
Source: The Register

George says
So how does registering that domain actually stop it. I mean why would WannaCry actually check to see if that domain is registered ?
Darknet says
As I mentioned in the article, it checks to see if it resolves, not if it’s registered, if an unregistered domain resolves that likely means the ransomware is running a sandbox and being forensically examined so it exits. The problem was WannaCry used a hardcoded domain not some random string to verify so once the domain was registered and always resolved, it would always exit, even when not in a sandbox.