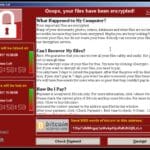
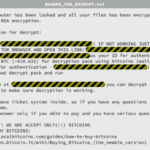
The latest ransomware kicking everyone’s ass is Gandcrab which has infected an estimated 50,000 computers, fortunately for the victims, Bitdefender has released a free Gandcrab ransomware decryption tool as a part of the No More Ransom Project. There’s nothing particularly notable about the ransomware itself other than it combines two existing exploit kits to compromise […]
Ransomware
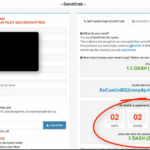
South Korean Webhost Nayana Pays USD1 Million Ransom
So far this Nayana payout is the biggest ransomware payment I’ve seen reported, there’s probably some bigger ones been paid but kept undercover. Certainly a good deal for the bad actors in this play, and well using an outdated Kernel along with PHP and Apache versions from 2006 you can’t feel too sorry for Nayana. […]
WannaCry Ransomware Foiled By Domain Killswitch
Whilst I was away on a tropical island enjoying myself the Infosec Internet was on fire with news of the global WannaCry ransomware threat which showed up in the UK NHS and was spreading across 74 different countries. The Ransomware seems to be the first that is P2P using an SMB exploit from the NSA […]
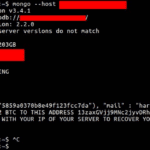
MongoDB Ransack – Over 33,000 Databases Hacked
Ah our favourite database in the news again, being hailed as the MongoDB Ransack a whole bunch of people have turned the insecure MongoDB default configuration into a ransom opportunity. They are deleting/stealing databases and soliciting bitcoin payments to return the data. With multiple actors doing the same stuff though it’s hard to know who […]
Mac OS X Ransomware KeRanger Is Linux Encoder Trojan
So there’s been a fair bit of noise this past week about the Mac OS X Ransomware, the first of its’ kind called KeRanger. It also happens to be the first popular Mac malware of any form for some time. It’s also a lesson to all the Apple fanbois that their OS is not impervious […]