It seems that 2016 has been the year of immense DDoS attacks, many coming from Mirai. This seems to be a newcomer though ending the year with a 650Gbps DDoS attack.
The Dyn DNS DDoS attack that some speculated reached over 1Tbps was probably the biggest, but this isn’t that far behind and it’s bigger than the previously largest recorded at 620Gbps.
As the end of the year approaches, it’s natural to contemplate the future and look for signs of things to come. Sometimes, however, you don’t have to search too hard. Sometimes, these “signs” hit you like a ton of bricks.
This is how it was for us when, just ten days before the year’s end, we found ourselves mitigating a 650 Gbps (Gigabit per second) DDoS attack—the largest on record for our network.
This was a fitting end to a year of huge DDoS assault, nasty new malware types and massive IoT botnets. What’s more, it showed exactly where things are heading next on the DDoS front.
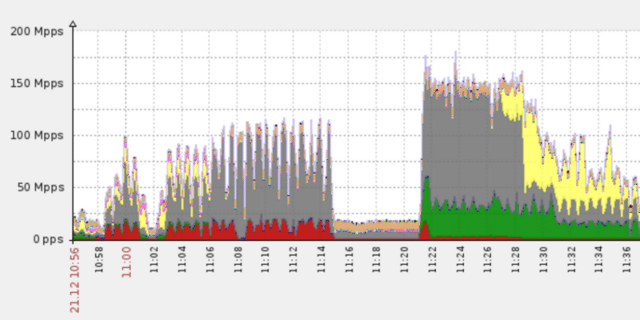
The attack began around 10:55 AM on December 21, targeting several anycasted IPs on the Imperva Incapsula network.
It’s hard to say why this attack didn’t focus on a specific customer. Most likely, it was the result of the offender not being able to resolve the IP address of his actual victim, which was masked by Incapsula proxies. And so, lacking any better option, the offender turned his attention to the service that stood between him and his target.
The attacks seems to have started out as an attack on an Incapsula customer and when failing with that, they moved onto attacking the service protecting them directly.
They mitigated the attack very well with minimal impact and it seems no downtime or customer impact.
The first DDoS burst lasted roughly 20 minutes, peaking at 400 Gbps. Failing to make a dent, the offender regrouped and came back for a second round. This time enough botnet “muscle” to generate a 650 Gbps DDoS flood of more than 150 million packets per second (Mpps).
This second burst lasted about 17 minutes and was just as easily countered by our service. Out of options, the offender wised up and ceased his assault.
Both attack bursts originated from spoofed IPs, making it impossible to trace the botnet’s actual geo-location or learn anything about the nature of the attacking devices.
The attack traffic was generated by two different SYN payloads:
- Regular-sized SYN packets, ranging from 44 to 60 bytes in size
- Abnormally large SYN packets, ranging from 799 to 936 bytes in size
The former was used to achieve high Mpps packet rates, while the latter was employed to scale up the attack’s capacity to 650 Gbps.
Whilst a pretty large attack, it’s certainly not the most persistent with the attacker giving up fairly easily and only using a few limited methods.
Either that, or they were just probing the Incapsula network to see what it could handle and didn’t want to expose their full hand.
Source: Incapsula Blog
