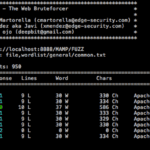
Wfuzz is a Python-based flexible web application password cracker or brute forcer which supports various methods and techniques to expose web application vulnerabilities. This allows you to audit parameters, authentication, forms with brute-forcing GET and POST parameters, discover unlinked resources such as directories/files, headers and so on. A brute force attack is a method to […]
Archives for May 2016
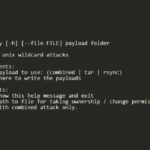
wildpwn – UNIX Wildcard Attack Tool
wildpwn is a Python UNIX wildcard attack tool that helps you generate attacks, based on a paper by Leon Juranic. It’s considered a fairly old-skool attack vector, but it still works quite often. The simple trick behind this technique is that when using shell wildcards, especially asterisk (*), the UNIX shell will interpret files beginning […]
CapTipper – Explore Malicious HTTP Traffic
CapTipper is a Python tool to explore malicious HTTP traffic, it can also help analyse and revive captured sessions from PCAP files. It sets up a web server that acts exactly as the server in the PCAP file and contains internal tools with a powerful interactive console for analysis and inspection of the hosts, objects […]
SubBrute – Subdomain Brute-forcing Tool
SubBrute is a community driven project with the goal of creating the fastest, and most accurate subdomain brute-forcing tool. Some of the magic behind SubBrute is that it uses open resolvers as a kind of proxy to circumvent DNS rate-limiting. This design also provides a layer of anonymity, as SubBrute does not send traffic directly […]
The Backdoor Factory (BDF) – Patch Binaries With Shellcode
The Backdoor Factory or BDF is a tool which enables you to patch binaries with shellcode and continue normal execution exactly as the executable binary would have in its’ pre-patched state. Some executables have built in protection, as such this tool will not work on all binaries. It is advisable that you test target binaries […]