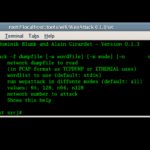
Gerix WiFi cracker is an easy to use Wireless 802.11 Hacking Tool with a GUI, it was originally made to run on BackTrack and this version has been updated for Kali (2018.1). To get it up and running make sure you do:
|
1 |
apt-get install qt4-dev-tools |
Running Gerix Wireless 802.11 Hacking Tool
|
1 |
$ python gerix.py |
You can download Gerix here: […]