Reaver download below, this tool has been designed to be a robust and practical tool to hack WPS Pin WiFi Networks using WiFi Protected Setup (WPS) registrar PINs in order to recover WPA/WPA2 passphrases.
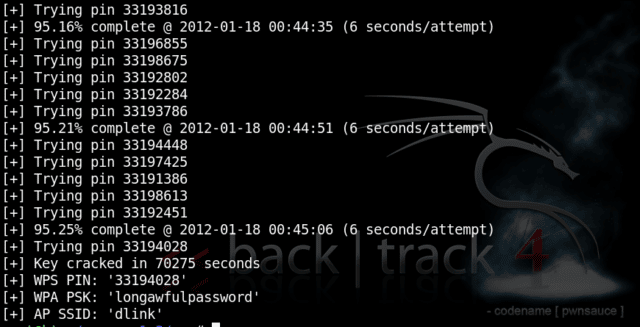
It has been tested against a wide variety of access points and WPS implementations.
The original Reaver implements an online brute force attack against, as described in here [PDF]. reaver-wps-fork-t6x version 1.6b is a community forked version, which has included various bug fixes and additional attack method (the offline Pixie Dust attack).
How to use Reaver
Depending on the target’s Access Point (AP), to recover the plain text WPA/WPA2 passphrase the average amount of time for the transitional online brute force method is between 4-10 hours. In practice, it will generally take half this time to guess the correct WPS pin and recover the passphrase. When using the offline attack, if the AP is vulnerable, it may take only a matter of seconds to minutes.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 |
Reaver v1.5.2 WiFi Protected Setup Attack Tool Copyright (c) 2011, Tactical Network Solutions, Craig Heffner <cheffner@tacnetsol.com> mod by t6_x <t6_x@hotmail.com> & DataHead & Soxrok2212 & Wiire Required Arguments: -i, --interface=<wlan> Name of the monitor-mode interface to use -b, --bssid=<mac> BSSID of the target AP Optional Arguments: -m, --mac=<mac> MAC of the host system -e, --essid=<ssid> ESSID of the target AP -c, --channel=<channel> Set the 802.11 channel for the interface (implies -f) -o, --out-file=<file> Send output to a log file [stdout] -s, --session=<file> Restore a previous session file -C, --exec=<command> Execute the supplied command upon successful pin recovery -D, --daemonize Daemonize reaver -a, --auto Auto detect the best advanced options for the target AP -f, --fixed Disable channel hopping -5, --5ghz Use 5GHz 802.11 channels -v, --verbose Display non-critical warnings (-vv for more) -q, --quiet Only display critical messages -K --pixie-dust=<number> [1] Run pixiewps with PKE, PKR, E-Hash1, E-Hash2, E-Nonce and Authkey (Ralink, Broadcom, Realtek) -Z, --no-auto-pass Do NOT run reaver to auto retrieve WPA password if pixiewps attack is successful -h, --help Show help Advanced Options: -p, --pin=<wps pin> Use the specified 4 or 8 digit WPS pin -d, --delay=<seconds> Set the delay between pin attempts [1] -l, --lock-delay=<seconds> Set the time to wait if the AP locks WPS pin attempts [60] -g, --max-attempts=<num> Quit after num pin attempts |
Deprecated and temporary left behind options
|
1 2 3 4 5 6 7 |
- n (reaver): Automatically enabled, no need to invocate it. - W (reaver): Temporary left behind. Integration of the default PIN generators was unstable, leading to many warnings at compilation time. It was also an issue to use a PIN attempt (risk of AP rating limit) in order to get a BSSID and an ESSID. For the moment PIN generation has to be done externally using the scripts provided in "doc". - a (reaver): This option was the only option which required sqlite3 adding an extra dependency. It was only designed for automation scripts and this task (execute the last reaver command again) can be easily done internally by the script that calls reaver - p1 and -p2 (reaver): Too much warnings and bugs. -H (reaver): There is a need to find a way to perform it more cleanly, work is in progress. - vvv (reaver): The highest level of verbose is temporary removed for the same reason. - g (wash): Option was broken in latest release and need to be seriously rethought. |
This fork supports the Pixie Dust attack which will work against modern routers, you can find a list of routers and which types of attack they are vulnerable to here.
There are other tools which rely on Reaver for WiFi hacking such as:
– wifite – Mass Wifi WEP / WPA Key Cracking Tool
– Fern Wifi Cracker – Wireless Security Auditing Tool
And don’t forget to check out:
– Hijacker – Reaver For Android Wifi Hacker App
Reaver Download – WPS Pin Hacking Tool
You can find the Reaver download here:
Or read more here.
