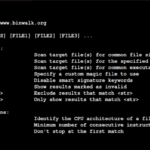
Binwalk is a fast and easy to use Python-based firmware security analysis tool that allows for firmware analysis, reverse engineering, and extraction of firmware images. Features of Binwalk Firmware Security Analysis & Extraction Tool Scanning Firmware – Binwalk can scan a firmware image for many different embedded file types and file systems File Extraction – […]
Hardware Hacking
ZigDiggity – ZigBee Hacking Toolkit
ZigDiggity a ZigBee Hacking Toolkit is a Python-based IoT (Internet of Things) penetration testing framework targeting the ZigBee smart home protocol. ZigBee continues to grow in popularity as a method for providing simple wireless communication between devices (i.e. low power/traffic, short distance), & can be found in a variety of consumer products that range from […]
CHIPSEC – Platform Security Assessment Framework For Firmware Hacking
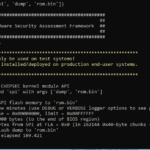
CHIPSEC is a platform security assessment framework for PCs including hardware, system firmware (BIOS/UEFI), and platform components for firmware hacking. It includes a security test suite, tools for accessing various low-level interfaces, and forensic capabilities. It can be run on Windows, Linux, Mac OS X and UEFI shell. You can use CHIPSEC to find vulnerabilities […]
US Voting Machines Hacked At DEF CON – Every One
US Voting Machines Hacked, some in minutes at this year’s DEF CON “Voting Village” – not something you want to hear really. Especially with the results of recent elections that the World is currently dealing with the consequences from. Of course with physical access, most machines can be dominated in some way or another – […]
DJI Firmware Hacking Removes Drone Flight Restrictions
Drones have been taking over the world, everyone with a passing interest in making videos has one and DJI firmware hacking gives you the ability to remove all restrictions (no-fly zones, height and distance) which under most jurisdictions is illegal (mostly EU and FAA for the US). It’s an interesting subject, and also a controversial […]