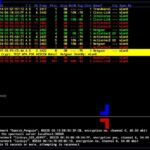
Kismet is an 802.11 layer2 wireless network detector, sniffer, and intrusion detection system. It will work with any wireless card which supports raw monitoring (rfmon) mode and can sniff 802.11b, 802.11a, and 802.11g traffic. What is Kismet? Kismet differs from other wireless network detectors in working passively. Namely, without sending any loggable packets, it is […]
wifi-jacking
Wi-Fi Jacking Extremely Common (45% of People Do!)
[ad] It seems Wi-Fi is actually extremely common, in fact in a recent poll up to 45% do it! I guess most people here have, I admit I do even with my phone when I’m out and about I’ll use any WiFi point that works. We can blame it on the manufacturers for having lax […]
Michigan Man Fined $400 for Using Coffee Shop’s Wi-Fi Network
[ad] Well this is a harsh turn of events, a while back an ‘ethics expert’ said Wifi Jacking is OK, now this poor guy has got pretty harshly screwed for using an open wireless connection from a nearby coffeeshop. A Michigan man has been fined $400 and given 40 hours of community service for accessing […]
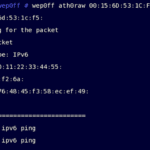
Wep0ff – Wireless WEP Key Cracker Tool
Wep0ff is new WEP Key Cracker that can function without access to AP, it works by mounting a fake access point attack against WEP-based wireless clients. It uses a combination of fragmentation and evil twin attacks to generate traffic which can be used for KoreK-style WEP-key recovery. This tool can be used to mount fake […]
Anonymity – Hiding Your Identity in 2006
Introduction Anonymity is derived from the greek word ἀνωνυμία (anonymia), meaning without a name or name-less. In colloquial use, the term typically refers to a person, and often means that the Ppersonal identity, or personally identifiable information of that person is not known. The main question is of course, what are you trying to hide? […]