Defence in depth for web applications is something that not many companies apply even though the model itself is nothing new. Defence in depth refers to applying security controls across multiple layers, typically Data, Application, Host, Internal Network, Perimeter, Physical + Policies/Procedures/Awareness.
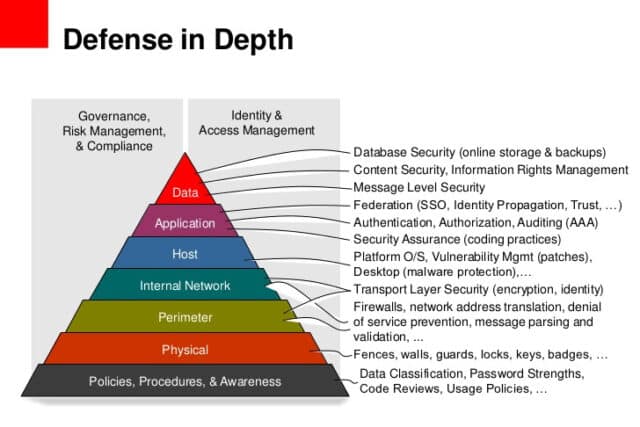
Defence in depth is a principle of adding security in layers in order to increase the security posture of a system as a whole. In other words, if an attack causes one security mechanism to fail, the other measures in place take arms to further deter and even prevent an attack.
Comprehensive strategies for applying the defence in depth principle extend well beyond technology and fall into the realm of the physical. These can take the form of appropriate policies and procedures being set up, training and awareness, physical and personnel security, as well as risk assessments and procedures to detect and respond to attacks in time. These measures, crucial though they might be, are only but physical measures to preventing what is ostensibly an information security problem.
This article on the other hand will focus on how defense in depth principles could apply to web applications and the network infrastructure they operate within. This article will also offer a number of pointers (that is by no means exhaustive) which can be used to improve the security of web applications.
Most of the points in the article would be classified as common sense if you are pretty experienced in the infosec line, but sadly as know all too well. Common sense is actually very uncommon and any organisation you probe will fail on multiple layers.
And yes, never, ever roll your own crypto implementation – even for hashing passwords. We’ve all seen how that’s turned out in the past.
Read the full article by Acunetix here: Defence in depth and how it applies to web applications
