WATOBO – The Web Application Security Auditing Toolbox – is intended to enable security professionals to perform highly efficient (semi-automated ) web application security audits.
It is capable of passive as well as active scanning and this latest is its real value added. It enables to automatize the discovery of common vulnerabilities (XSS, LFI, SQL injections etc) in web applications.
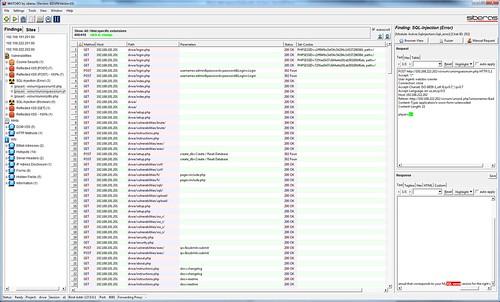
WATOBO works like a local proxy, similar to ZAP, Paros or Burp Suite but in Ruby, when the rest are pretty much in JAVA.
Features
- WATOBO has Session Management capabilities! You can define login scripts as well as logout signatures. So you don’t have to login manually each time you get logged out.
- WATOB can act as an transparent proxy
- WATOBO has anti-CSRF features
- WATOBO can perform vulnerability checks out of the box.
- WATOBO supports Inline De-/Encoding, so you don’t have to copy strings to a transcoder and back again. Just do it inside the request/response window with a simple mouse click.
- WATOBO has smart filter functions, so you can find and navigate to the most interesting parts of the application easily.
- WATOBO is written in (FX)Ruby and enables you to easiely define your own checks
- WATOBO is free software ( licensed under the GNU General Public License Version 2)
Scanning/Active Checks
During a scan all selected active modules will be used to test the one or more chats (chat = request/response pair). The total amount of resulting requests is hard to predict because in most cases it depends on the number of parameters and the module itself. Here’s the list of the currently available active checks:
- Server-Status page
- Directory Walker
- FileExtensions
- HTTP Methods
- Lotus Domino DB Enumeration
- .NET Custom Error
- .NET Files
- Local File Inclusion
- Crossdomain Policy
- Basic JBoss enumeration
- SAP ITS: Default Commands
- SAP ITS: Default Services
- SAP ITS: Service Parameters
- SAP ITS: XSS
- Siebel Applications
- Error-based SQL-Injection
- Time-based SQL Injection
- Boolean SQL-Injection
- Numerical SQL-Injection
- XML-XXE
- NextGeneration Cross Site Scripting Checks
- Simple Cross Site Scripting Checks
You can download WATOBO 0.9.20 gem here:
Or read more here.
