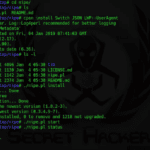
Nipe is a Perl script to make Tor default gateway for network, this script enables you to directly route all your traffic from your computer to the Tor network through which you can surf the internet anonymously without having to worry about being tracked or traced back. Tor enables users to surf the internet, chat […]
tor
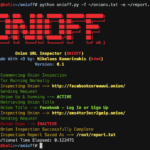
ONIOFF – Onion URL Inspector
ONIOFF is basically an Onion URL inspector, it’s a simple tool – written in pure python – for inspecting Deep Web URLs (or onions). It takes specified onion links and returns their current status along with the site’s title. It’s compatible with Python 2.6 & 2.7. Usage
|
1 |
Usage: python onioff.py {onion} [options] |
To view all available options run:
|
1 |
$ python onioff.py -h |
[…]
Exitmap – Tor Exit Relay Scanner
Exitmap is a fast and modular Python-based Tor exit relay scanner. Exitmap modules implement tasks that are run over (a subset of) all exit relays. If you have a background in functional programming, think of exitmap as a map() interface for Tor exit relays. Modules can perform any TCP-based networking task; fetching a web page, […]
Drones, Tor & Remailers – The Story Of A High-Tech Kidnapping
This whole thing sounds like something straight out of CSI: Cyber with references to Drones, Tor, remailers, anonymous image sharing and the scrubbing of meta data. Pretty interesting reading, although it rather smells like a lot of exageration. A super high-tech kidnapping – gone wrong in the end. Whoever wrote tho e-mails sent to the […]
Bitcoin Not That Anonymous Afterall
One of the big advantages touted by Bitcoin (and other cryptocurrencies) was always the anonymity of the transactions, yes you can track a wallet address and see the transaction history. But there’s no real way to link that wallet address to a real person (so we thought). I mean other than any leaky fiat exchange […]