OWASP Mutillidae II is a free, open source, deliberately vulnerable web-application providing a target for web-security enthusiest to learn web hacking. Mutillidae can be installed on Linux and Windows using LAMP, WAMP, and XAMMP for users who do not want to administrate a webserver. It is pre-installed on SamuraiWTF, Rapid7 Metasploitable-2, and OWASP BWA. The […]
owasp
OWASP Bricks – Modular Deliberately Vulnerable Web Application
Bricks, a deliberately vulnerable web application built on PHP & MySQL focuses on variations of commonly seen application security vulnerabilities & exploits, which can be exploited using tools (Mantra & ZAP). The mission is to ‘break the bricks’. Road Map Demonstrate maximum variations of most common vulnerabilities Help people to learn the need of secure […]
TLSSLed v1.2 – Evaluate The Security Of A Target SSL Or TLS (HTTPS) Web Server Implementation
When running web application security assessments it is mandatory to evaluate the security stance of the SSL/TLS (HTTPS) implementation and configuration. OWASP has a couple of references the author strongly recommends taking a look at, the “OWASP-CM-001: Testing for SSL-TLS” checks, part of the OWASP Testing Guide v3, and the Transport Layer Protection Cheat Sheet. […]
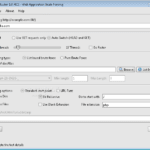
DirBuster Download – Brute Force Directories & Files Names
DirBuster download below, this is another great tool from the OWASP chaps, it’s basically a multi threaded java application designed to brute force directories and files names on web/application servers. Often is the case now of what looks like a web server in a state of default installation is actually not, and has pages and […]
Zed Attack Proxy – ZAProxy v1.3.0 Released – Integrated Penetration Testing Tool
It’s been a while since the last time we wrote about the OWASP ZAP – Zed Attack Proxy for Web Application Penetration Testing, back in October 2010. ZAP is an easy to use integrated penetration testing tool for finding vulnerabilities in web applications. It is designed to be used by people with a wide range […]