DirBuster download below, this is another great tool from the OWASP chaps, it’s basically a multi threaded java application designed to brute force directories and files names on web/application servers.
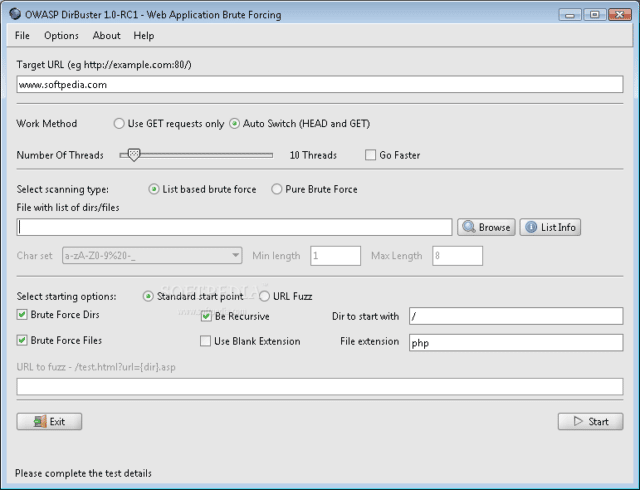
Often is the case now of what looks like a web server in a state of default installation is actually not, and has pages and applications hidden within – it attempts to find these.
What makes OWASP DirBuster different?
However tools of this nature are often as only good as the directory and file list they come with. A different approach was taken to generating this. The list was generated from scratch, by crawling the Internet and collecting the directory and files that are actually used by developers!
The tool comes a total of 9 different lists (Further information can be found below), this makes it extremely effective at finding those hidden files and directories. And if that was not enough it also has the option to perform a pure brute force, which leaves the hidden directories and files nowhere to hide! If you have the time ;)
What DirBuster can do for you
– Attempt to find hidden pages/directories and directories with a web application, thus giving another attack vector (For example. Finding an unlinked to administration page).
What DirBuster will not do for you
– Exploit anything it finds. This is not the purpose of this tool. It’s sole job is to find other possible attack vectors.
How does DirBuster help in the building of secure applications?
– By finding content on the web server or within the application that is not required.
– By helping developers understand that by simply not linking to a page does not mean it can not be accessed.
DirBuster Download
You can download here:
Linux – DirBuster-0.12.tar.bz2
Windows – DirBuster-0.12-Setup.exe
Mac – DirBuster-0.11.1.dmg
Or read more here.
