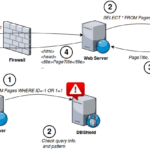
DBShield is a Database Firewall written in Go that has protection for MySQL/MariaDB, Oracle and PostgreSQL databases. It works in a proxy fashion inspecting traffic and dropping abnormal queries after a learning period to populate the internal database with regular queries. Learning mode lets any query pass but it records information about it (pattern, username, […]
database-security
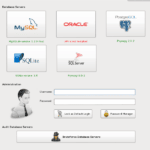
HexorBase – Administer & Audit Multiple Database Servers
HexorBase is a database application designed to administer and to audit multiple database servers simultaneously from a centralised location, it is capable of performing SQL queries and brute-force attacks against common database servers (MySQL, SQLite, Microsoft SQL Server, Oracle, PostgreSQL). It allows packet routing through proxies or even Metasploit pivoting antics to communicate with remotely […]
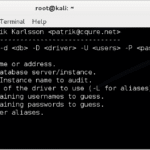
DBPwAudit – Database Password Auditing Tool
DBPwAudit is a Java database password auditing tool that allows you to perform online audits of password quality for several database engines. The application design allows for easy adding of additional database drivers by simply copying new JDBC drivers to the jdbc directory. Configuration is performed in two files, the aliases.conf file is used to […]
ODAT (Oracle Database Attacking Tool) – Test Oracle Database Security
ODAT (Oracle Database Attacking Tool) is an open source penetration testing tool that test Oracle database security remotely. Usage examples of ODAT: You have an Oracle database listening remotely and want to find valid SIDs and credentials in order to connect to the database You have a valid Oracle account on a database and want […]
Navy Sys Admin Hacks Into Databases From Aircraft Carrier
So this story caught my eye and I found it pretty interesting as it reads like something out of a Tom Clancy novel crossed with a bunch of script kiddies, a Navy Sys Admin has been charged with conspiracy to hack – the interesting part was that he hacked the Navy (whilst working there..) and […]