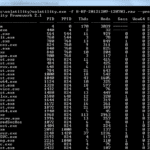
The Volatility Framework is an an advanced, completely open collection of tools for memory forensics, implemented in Python under the GNU General Public License, for the extraction of digital artifacts from volatile memory (RAM) samples. The extraction techniques are performed completely independent of the system being investigated but offer visibility into the runtime state of […]
Security Software
Emerging Threats ETOpen – Anti-malware IDS/IPS Ruleset
The ETOpen Ruleset is an excellent anti-malware IDS/IPS ruleset that enables users with cost constraints to significantly enhance their existing network-based malware detection. The ETOpen Ruleset is not a full coverage ruleset, and may not be sufficient for many regulated environments and should not be used as a standalone ruleset. The ET Open ruleset is […]
Bearded – Security Automation Platform
Bearded is an open source Security Automation platform. The platform allows Development, QA, and Security team members to perform automated web security scans with a set of tools, and re-execute those scans as needed. All tools can be executed in the cloud in docker containers. Bearded has a default web interface which integrates all core […]
OpenIOC – Sharing Threat Intelligence
OpenIOC is an open framework for sharing threat intelligence, sophisticated threats require sophisticated indicators. In the current threat environment, rapid communication of pertinent threat information is the key to quickly detecting, responding and containing targeted attacks. OpenIOC is designed to fill a void that currently exists for organizations that want to share threat information both […]
Cuckoo Sandbox – Automated Malware Analysis System
Cuckoo Sandbox is Open Source software for automating analysis of suspicious files. To do so it makes use of custom components that monitor the behaviour of the malicious processes while running in an isolated environment. In other words, you can throw any suspicious file at it and in a matter of seconds Cuckoo will provide […]